100+ Data Privacy and Data Security Statistics You Need to Watch

Data privacy and security are in a peculiar state in recent years.
We’re currently experiencing an unprecedented level of threats targeting our data, whether that’s vulnerable big data stores or hacking attacks. Yet, in the same breath, cybersecurity practices, regulations, technologies, and general cyber awareness are at their best.
Data privacy, for that matter, is not a uniquely modern-day conundrum. The first “Right to Privacy” was conceived in 1890 by 2 American lawyers, Samuel D. Warren and Louis Brandeis. Perhaps it’s not extreme to suggest humans have been grappling with privacy issues for as long as civilization itself.
Now, in the 21st Century, technology puts the world in our hands and unlimited amounts of information at the end of our fingertips. But what price do we pay to enjoy the benefits of the information age? And are data privacy and security practices doing enough? To help unpack that question a little further, we’ve compiled 100+ data privacy and data security statistics.
We’ll delve into the world of privacy issues, objections, risks, and regulations in this article. But before we get into our assortment of statistics, it’s probably best we take a look at some key definitions first. Data privacy and data security are 2 good places to start…
What is Data Privacy & Data Security?
Data privacy, also known as information privacy, is the area of data protection concerned with regulations. In particular, data privacy outlines the ways companies/individuals should properly collect, share, and use sensitive, personal, and/or confidential data (such as financial records or intellectual properties) in line with the law.
Data security is more about the practice of protecting data. If data privacy is “what” you should/shouldn’t do with data, data security is “how” you’re going to make sure data is protected.
Data security covers every way data handlers can avoid the unauthorized access, theft, or corruption of digital information from bad actors. This includes a range of practices, from the physical security of hardware and storage devices to the authentication controls on servers, networks, and devices.
Data security also includes each organization’s policies and procedures. If done correctly, proper data security strategies prevent data compromise and attempts to steal data from cybercriminals.
When we talk about these terms together, then, we are talking about the general state of data protection — both with regards to the legislation that protects our data and the companies or individuals that handle it.
General Stats
As you probably already know, everyone wants your data. Companies want it, governments want it, and (worst of all) criminals want it. Knowledge is power, after all.
We’ll begin with a few general statistics on the state of data protection and data collection.
1. We Generate a Lot of Data

Humans are generating vast quantities of data every day.
With so much data available, it makes sense for companies to capitalize. They can use data to improve your customer experience, target you with the right marketing materials, sell your data to make money, or use that data to provide other services.
2. People Want Online Security

Woah! Easy there, tiger… Perhaps there’s no better way to set the mood than with the statement above.
Given how much people love that other thing, they must be pretty unsatisfied with their online security to consider giving it up. This points to the sorry state of online security and the desperation users have to keep their data secure.
3. Data Collection is Unavoidable
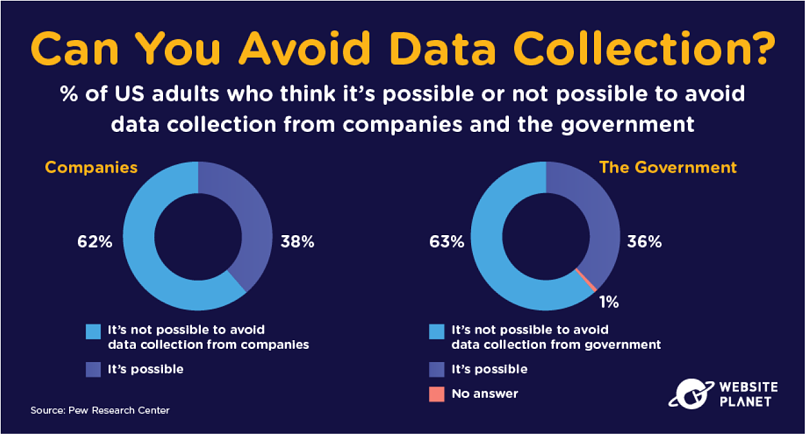
So data security isn’t quite perfect, but we can just flat-out refuse to let entities take our data — right?
Well, technically, you can, although not really. The secret has been revealed ever since Edward Snowden blew his whistle on the shifty practices of the National Security Agency (NSA): you’re tracked, whether you like it or not.
4. Data Is Uncontrollable

As important as it is to control our data, the fact of the matter is that we don’t have much control.
“Read this,” “sign this,” “agree to this” — otherwise, you can’t use company X’s essential service.
Once organizations have your data, they can sell it to third parties — all while you struggle to remember providing consent.
5. How Much Data Do Companies Collect?
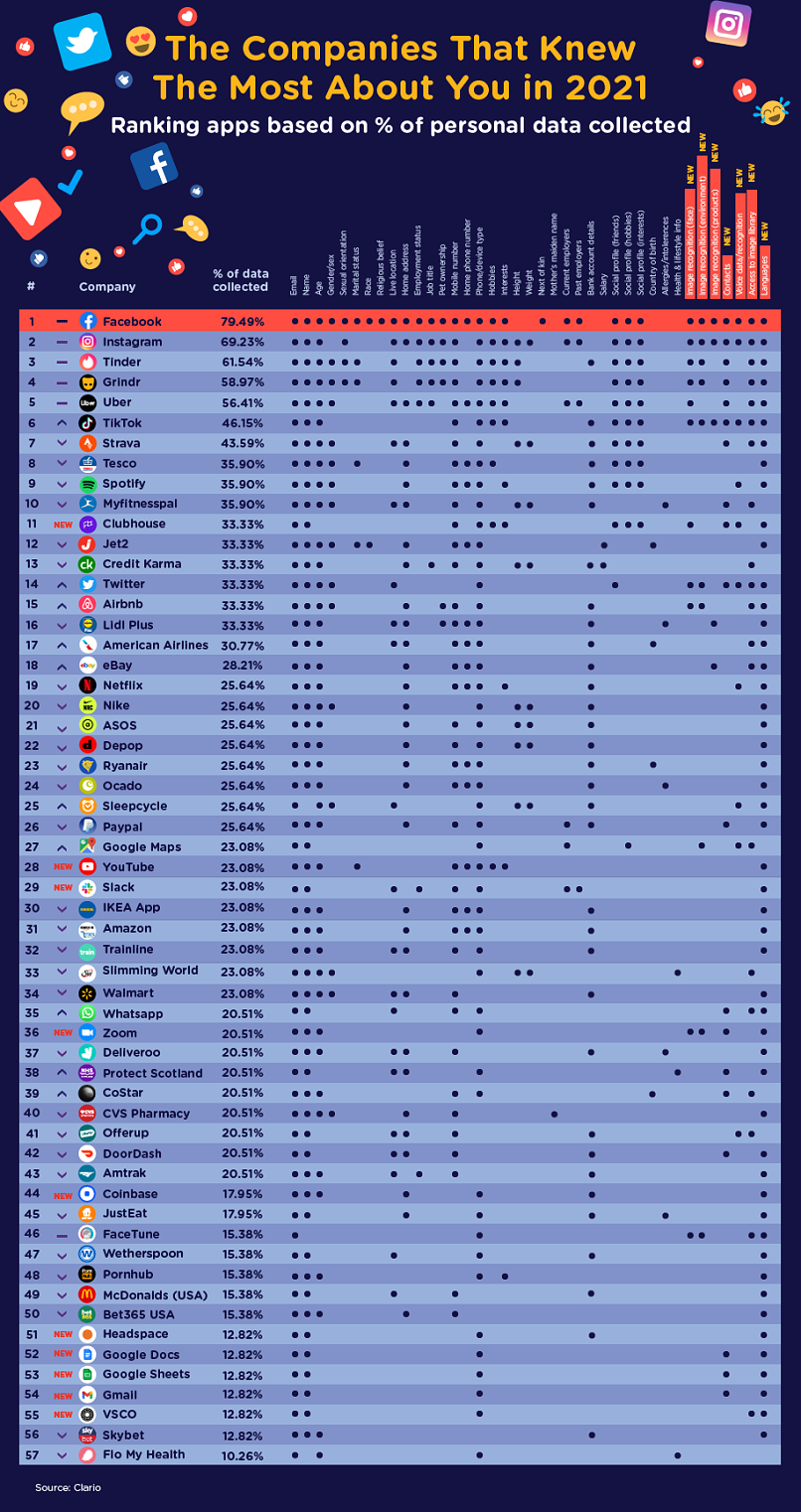
The amount (and type) of personal data that’s collected from you will change company-to-company.
Facebook and Instagram are 2 apps that track users more than any other. Facebook, in particular, collects 79% of your personal data.
6. Whose Data Is Collected?
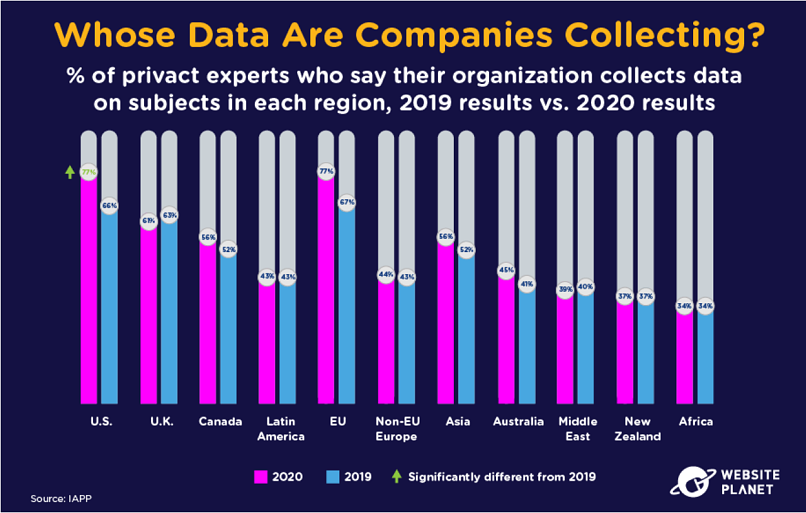
U.S. citizens are targeted by data collectors more than citizens of any other nation. This should hardly be surprising, given the country’s vast population and consumer-centric culture of commerce.
7. Companies Collect Data for Personalization
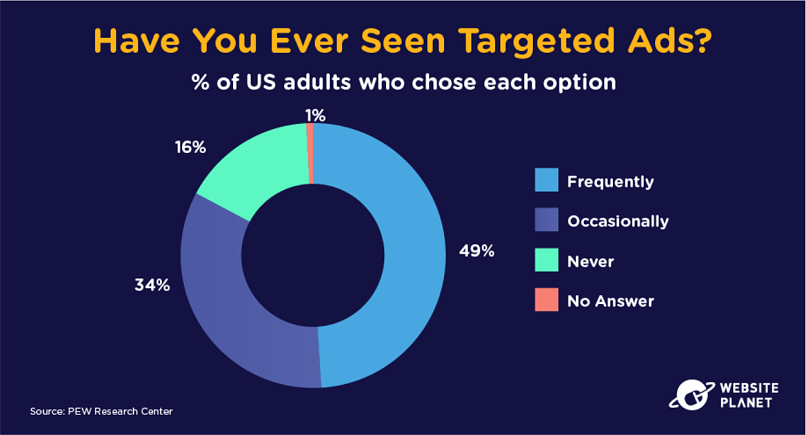
According to pCloud, 80% of apps use your data to sell you more products/services. The more a business knows about the way you are and the stuff you like to do, the more that company can target you with products they believe you will enjoy.
This level of personalization is a no-brainer, especially when 66% of consumers expect businesses to understand their wants and needs (Salesforce). Data is the key to personalization.
8. Data Analytics
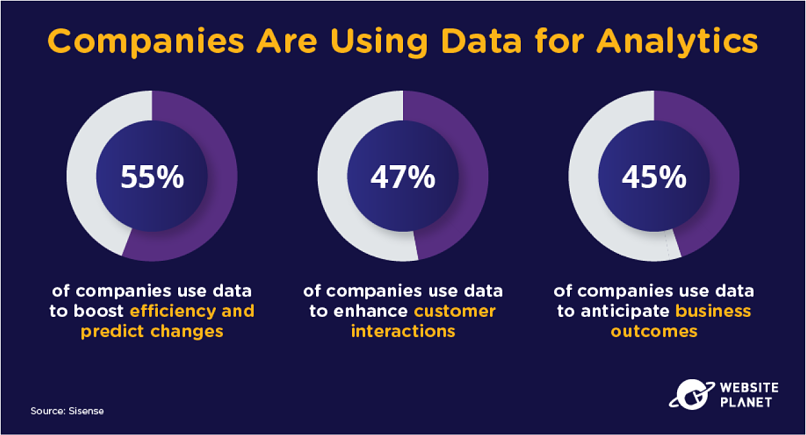
Companies are not only collecting data to sell you more stuff. Data can be used for analytics too.
User data provides businesses with feedback on overall performance to teach businesses the areas in which they can improve their strategy, operate more efficiently, and maximize profit margins.
9. Third-Party Sharing

Your data is also passed on to third parties. This is another way companies can make money: by sharing your preferences, habits, and other forms of PII (personally identifiable information).
Governments may purchase data from certain services, and companies will buy your data to see if you’re a potential customer. That’s just the way things work.
10. Big Data = Less Secure

This corporate race for your information has given birth to “big data.” Big data describes the enormous sets of data that companies now collect, store, and analyze. Big data stores are an attractive target for hackers, as vast quantities of data can be mishandled at once.
11. Cookies Fuel Big Data

Sure, we often provide companies with our data on sign-up forms or during orders, but you’re being tracked in other ways too. Cookies allow companies to track your online behavior and preferences, whether you’re surfing on the companies own site or not.
12. The Government Accesses Your Data
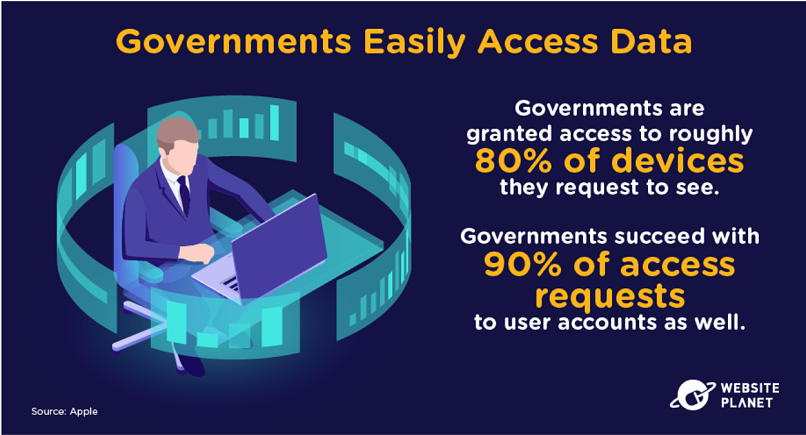
When the government requests access to your data, they usually get it. The government might want your data to help solve a crime investigation or aid a public safety incident.
13. Big Tech Tracks Your Web Traffic
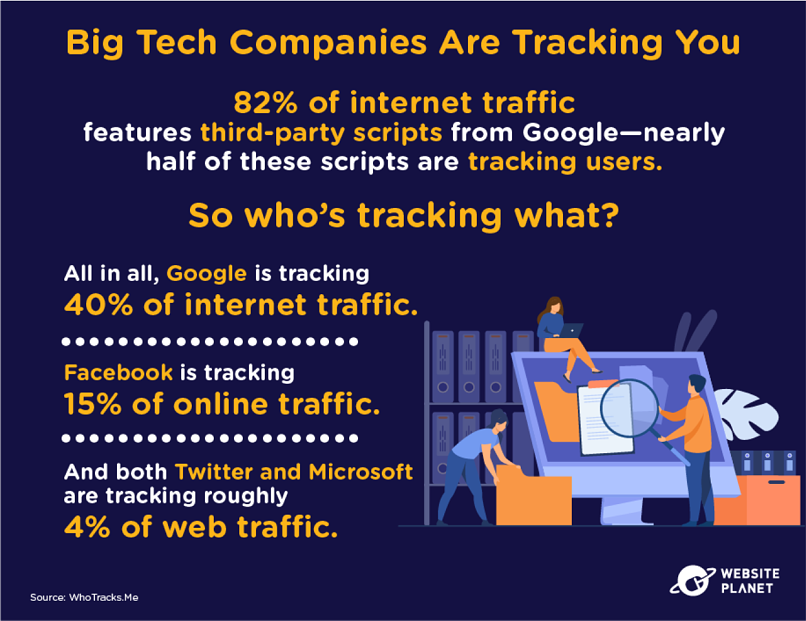
Big tech companies are particularly interested in your data. These companies operate online, which provides them with ample opportunities to collect, store, analyze, and share insights from your web traffic.
14. How Common Are Attacks on Our Data?

Attacks on our data are painfully common. There is a hacker attack on a computer every 39s, and hackers conduct a ransomware attack every 14s.
Big data stores bear the brunt of security incidents, but that’s not to say our personal devices aren’t under threat. 50% of U.S. adults have suffered from malware or a virus on their personal computers (Security.org).
15. The Remote Work Factor

Remote work has undoubtedly affected the security and safety of our data. Remote work isolates employees from their colleagues and makes them vulnerable to social engineering, phishing, or even hacks on their network/devices.
16. COVID-19 has increased threats to your data
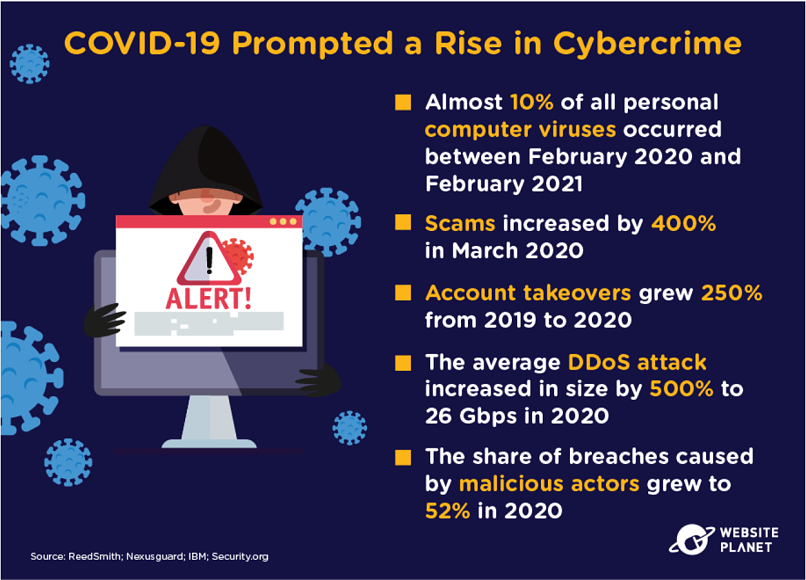
COVID-19 has increased the volume of cyberattacks targeting data. Remote work has been a big motivator for cybercrime, along with all of the valuable information in circulation during COVID-19, such as medical records, which are targeted by cybercriminals.
Data Breaches
A data breach occurs when protected sensitive, personal, private, and/or confidential information is exposed to an unsecured or untrusted environment.
Data breaches can be intentional or unintentional. If data is exposed to the wrong kind of people, breaches can be extremely damaging too.
17. How Many Data Breaches Are There?

There are thousands of data breaches every year, and these incidents leak billions of customer records. If you need comforting about the security of your personal data, these stats probably don’t fill you with confidence.
18. Average Size of A Breach?

Data breaches leak nearly 26,000 records on average. Smaller breaches of personal devices might leak a handful of your records. Mega leaks on big data stores can expose billions of customers in a single incident.
19. Which Data Is Targeted & Leaked?
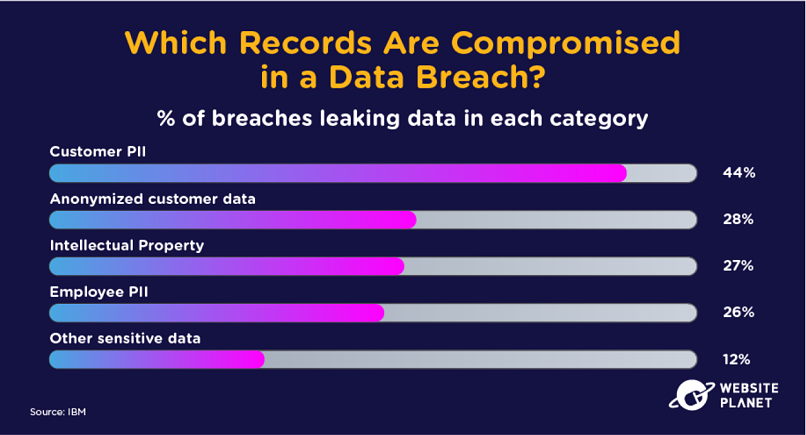
Customer PII (personal data), which includes information like names, addresses, and social security numbers, is exposed in the vast majority of breaches. Companies typically collect PII, and it’s worth a lot to cybercriminals.
20. The Average Breach Lifecycle
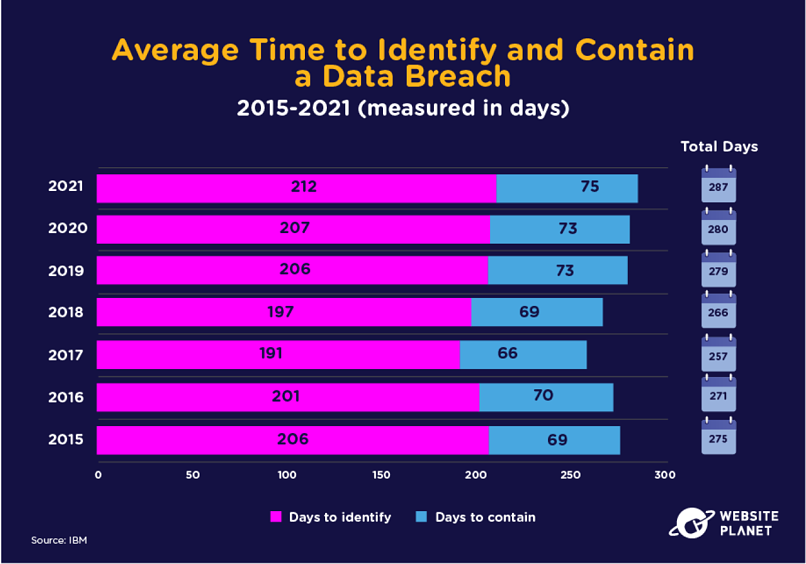
Data breaches at organizations take a long time to identify and close. There are numerous audits, analyses, compensations, and communications that must be conducted following the discovery of a breach.
21. The Cost of a Data Breach
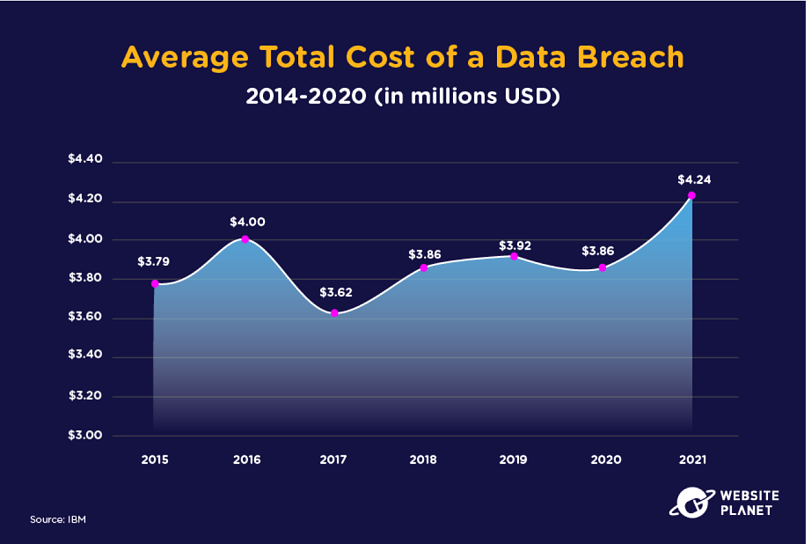
Breach costs have remained relatively consistent for businesses over several years, though costs have increased under the security pressures of a pandemic.
Data breach costs across different industries or even nations can differ greatly.
For example, the healthcare industry suffers the costliest average breach damages of all sectors ($9.23 million) due to its vast stores of sensitive medical records. The USA is the nation with the highest average breach costs, at $9.05 million.
22. The Costliest Data to Lose
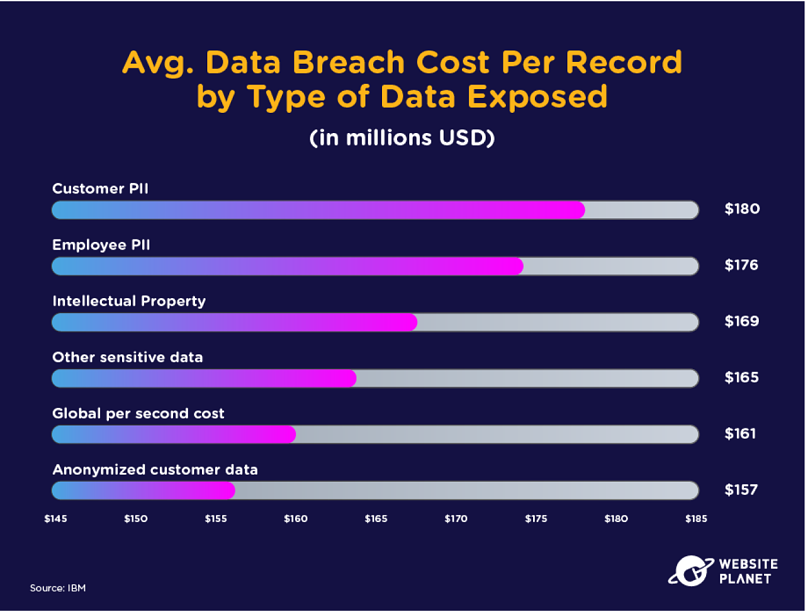
Companies have to pay around $160 for every stolen record they lose (on average). Customer PII (especially PII taken maliciously) costs businesses more because it can directly expose users to cybercrime.
23. Cyber Insurance Recovers Costs
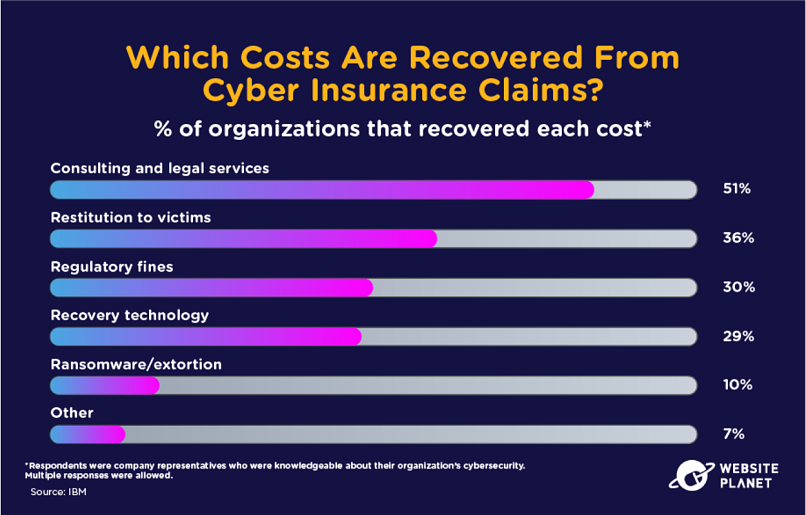
Some breach costs can be recovered through cyber insurance. 75% of organizations have cyber insurance. The total value of cyber insurance premiums around the world could reach $20 billion by 2025.
24. Who Causes Data Breaches?
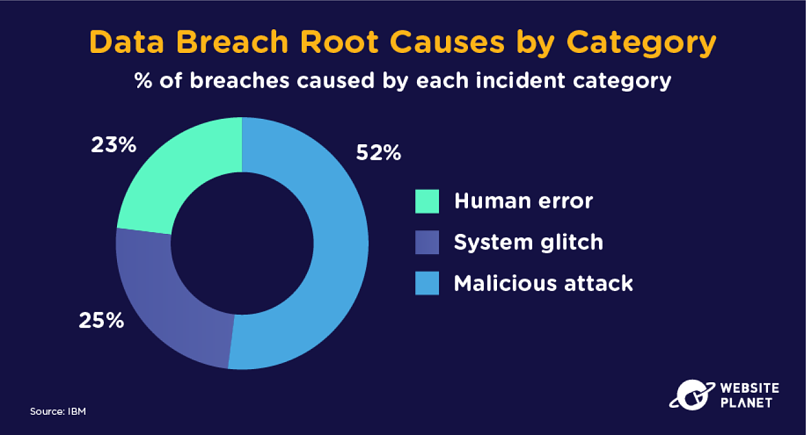
Malicious actors are behind the majority of data breaches. System glitches (25%) and human error (23%) also play a part but, more often than not, cyberattacks cause data breaches.
25. Malicious Motivations
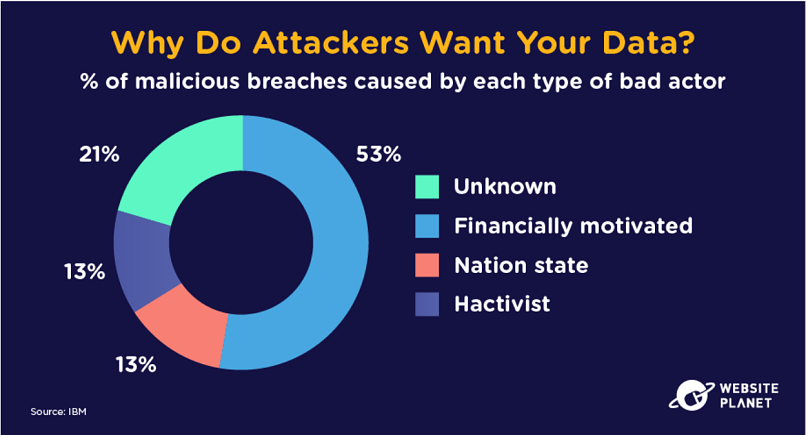
What do malicious actors want with your data, exactly?
Malicious actors can have a bunch of different motivations for stealing your data. They may need it for an activist cause, or they may target your data to disrupt another organization. Hackers could even go after data to get information for their state.
53% of data breaches, however, are financially motivated. This means hackers are stealing data for scams and fraud. Did you know? Cybercriminals can earn up to $2.2 million when stealing just 10 credit card records per website in formjacking attacks.
26. What Causes Data Breaches?
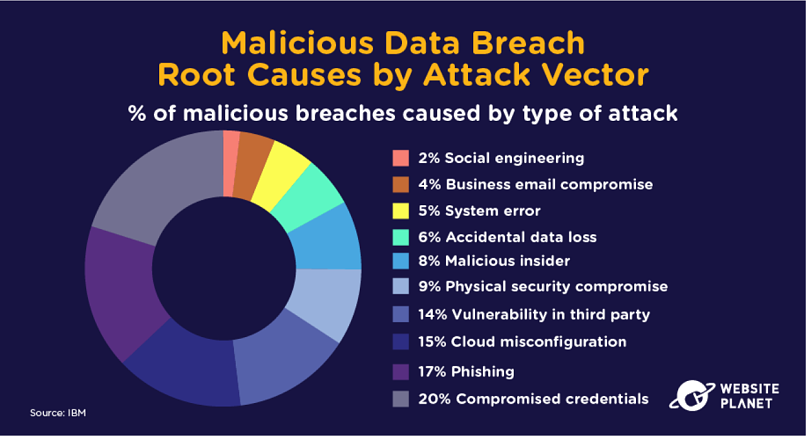
Hackers can utilize loads of different methods in a malicious attempt on your data. Phishing, third-party software vulnerabilities, cloud misconfigurations, and compromised credentials are the 4 biggest ways hackers access your data.
27. Poor Knowledge Leads to Poor Cybersecurity Hygiene

Most employees lack basic knowledge of data privacy and security. This is the defining factor in human error breaches, misconfigurations, misdeliveries, and social engineering attacks — employees make a mistake that leads to a breach.
Companies understand that this is a big issue. No wonder businesses are collectively spending $1 billion a year on cybersecurity awareness training.
28. Insider Threat Motivations
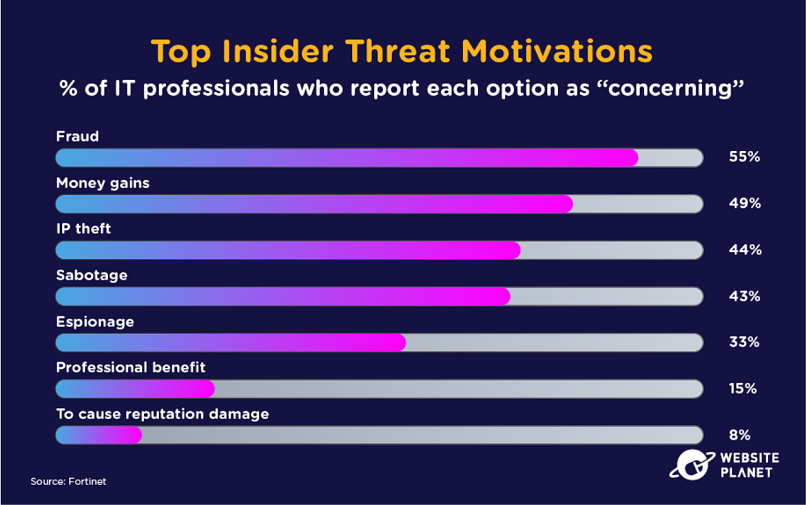
Businesses struggle to account for insider threats. Malicious employees can turn on organizations at any moment, and, unfortunately, there’s not a lot businesses can do outside of conducting background screening on new recruits.
According to Haystax, unavoidable data breaches are a concern for 70% of organizations — that’s unsurprising when we consider that insider threats grew 47% between 2018 and 2020.
29. Ransomware Is the Prevalent Malware

Malware is a big problem. According to Mimecast, 74% of organizations have suffered a malware attack that spread between employees in 2021.
Malware is any type of malicious software. It can come in the form of Trojans, infostealers, spyware, and so many more varieties, but the most popular form of malware right now is ransomware. Ransomware can hold your data hostage until a ransom is paid.
30. Phishing Is Common

Phishing attacks are the most common cyberattack. Cybercriminals can often coerce an array of personal data out of victims when posing as a trustworthy entity.
According to Avanan, harvesting your credentials was the focus of 54% of phishing attacks in 2020. 20.7% of phishing attacks exploit top-level employees in business email compromise (BEC), while 2.2% of phishing attacks involve extortion.
31. Hackers Use Credentials & Brute Force

Credential-based attacks and brute-force attacks bypass security authentication by gaining access to user accounts.
These are popular methods for hackers. Cybercriminals can buy stolen credentials online, saving them the time and hassle of acquiring information in a hack. Brute-force attacks input countless password and username combinations.
32. The Biggest Breaches
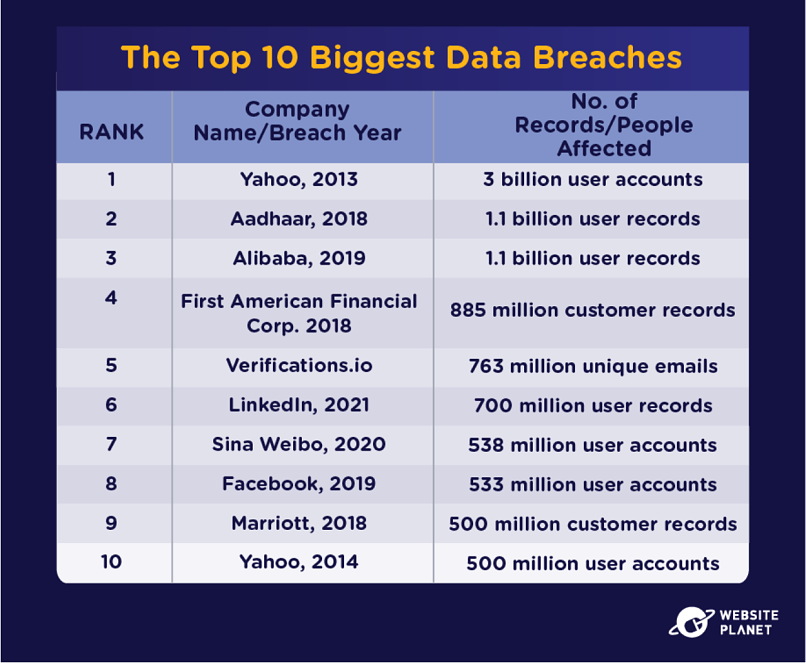
The biggest data breaches expose billions of unique customer records. Yahoo rounds out either side of the top 10 biggest data breaches with 3.5 billion users impacted over 2 years.
CAM4’s 2020 data breach deserves a mention. The adult streaming platform leaked a staggering 10.88 billion records, although this exposure “only” impacted around 11 million unique customers.
Data Risks
Your data is at risk of malicious actors, ad tracking, and data leaks. Where is your data most vulnerable? What systems leak data? And what information do hackers target?
33. Your Data Is Vulnerable
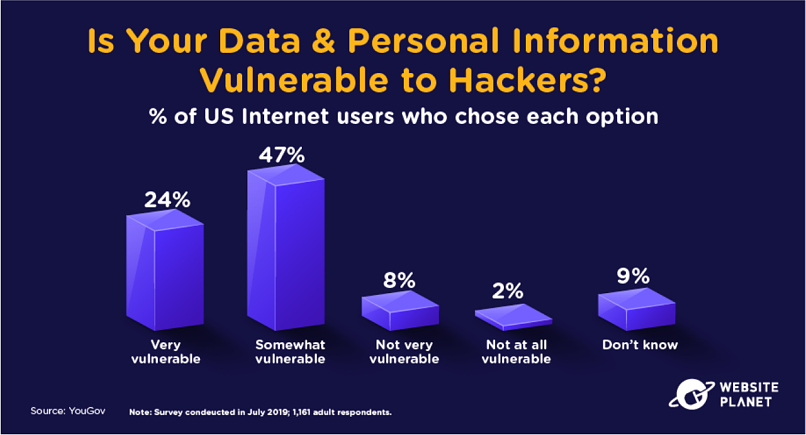
Your data is vulnerable to the threat of malicious actors, system glitches, and human error.
Customer data is especially vulnerable to social engineering or hacking.
41% of companies store more than 1,000 sensitive files that are accessible to every employee. This includes credit card records, health records, and other forms of PII. The figure is even higher for financial companies, at 64%.
Varonis found that nearly 60% of companies keep 1,000+ folders with inconsistent permissions, making files susceptible to bad actors.
34. Out of Control Data
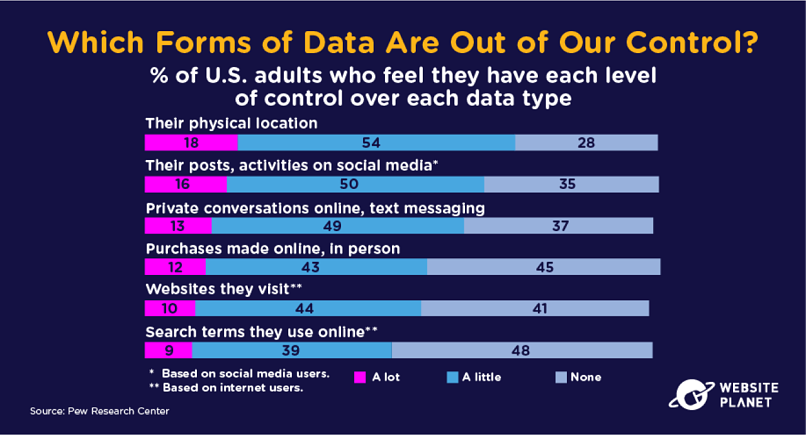
We’ve established that users feel like they don’t have control of their data, but which types of data are the most difficult to keep private?
Nearly 50% of internet users feel like they have no control over who sees their search terms. Search terms can be used to judge a user’s preferences and personalize their online experience.
35. The Most Sensitive Data
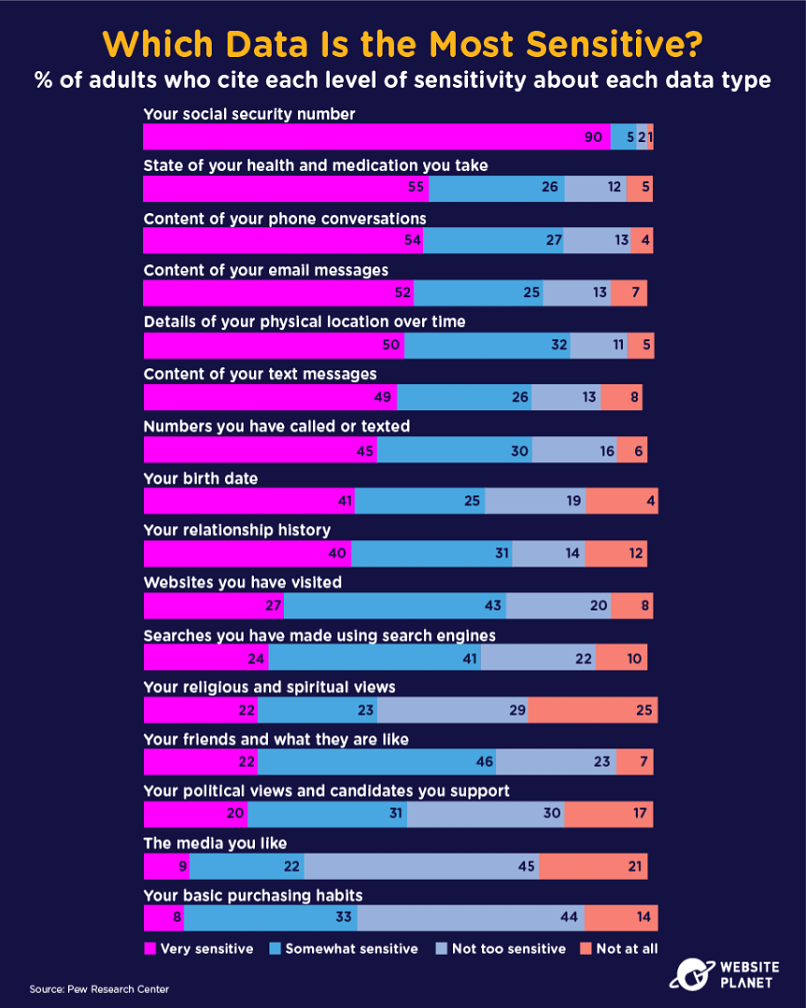
Social security numbers are the most sensitive piece of information you could lose in a data breach. Hackers target this data as its unchangeable PII: details that criminals could use to commit identity theft and fraud for years to come.
Elsewhere, medical history and phone conversations are also seen as highly sensitive data.
36. When’s Your Data Most at Risk?
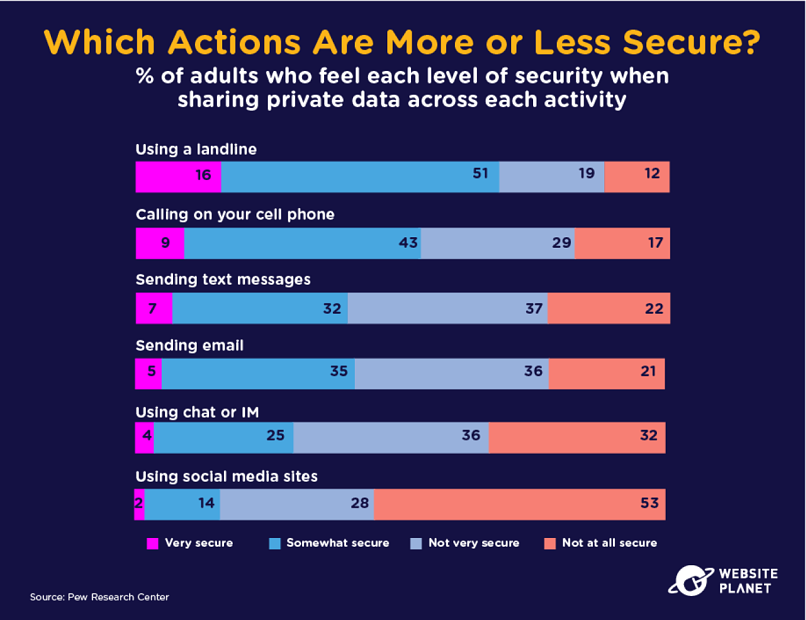
People generally feel most secure when on the phone, either using a landline or mobile.
Email and chat services are listed as a risk, while social media sites check out as the least secure platform in the eyes of internet users. There are now over 4 billion social media users. Between email and social media, 21% of users have experienced at least one cyberattack.
37. Public WiFi Is a Risk
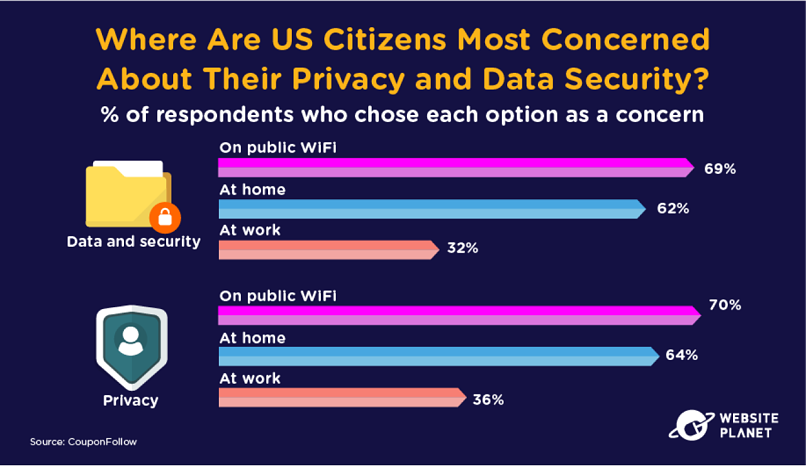
US internet users ranked public WiFi as the most concerning location for data security and privacy. Public WiFi often requires very weak (or non-existent) authentication, and hackers can target data through public WiFi as a result.
38. Social Media Is Compromised

Social media users face several data security risks, from phishing attempts and scams in instant messaging platforms to adverts infected with malware.
One of the biggest risks social media users face is account takeover. Account takeover occurs on social media platforms more than anywhere else.
39. IoT Devices Are Super Vulnerable
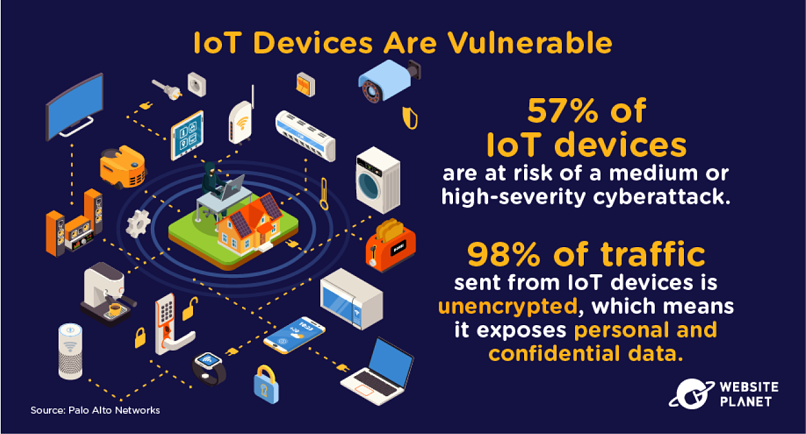
IoT describes the “Internet of Things” — a network of connected everyday devices that share data with other devices and systems. Examples of IoT devices include heart sensors that relay data back to doctors, or smart kettles that can be turned on via a mobile phone.
Unfortunately, IoT devices have an extremely poor level of cybersecurity. IoT devices are set to reach 75 billion by 2025, so this needs fixing sooner than later.
40. Websites & Web Apps Leak Data

Websites and web apps are vulnerable to hacks too. Almost every website is thought to have a vulnerability that could be exploited by hackers.
Website vulnerabilities are indeed regularly exploited by hackers, for that matter. 30,000 new websites are hacked daily.
41. Mobile Vulnerabilities

A huge portion of mobile devices could be vulnerable to cyberattacks. Older mobile devices often use older iterations of operating systems, such as iOS and Android, which leaves them open to attack.
42. Mobile Apps Are Open to Attack
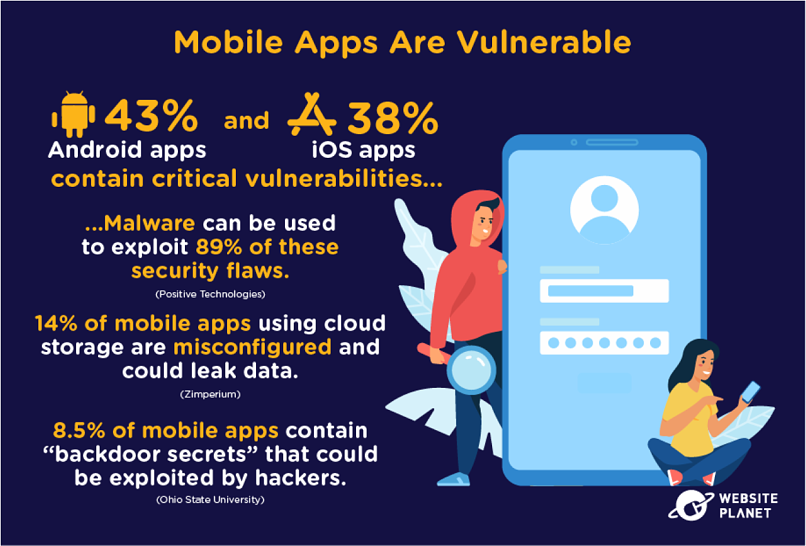
Mobile apps are a prevailing threat to personal cybersecurity. Millions of apps are thought to contain vulnerabilities, insecure configurations, or may even be harboring Trojan malware.
Mobile apps can affect data security at businesses too. According to Checkpoint, 46% of companies have one or more employees with a malicious mobile app on their devices.
43. Public Cloud Security
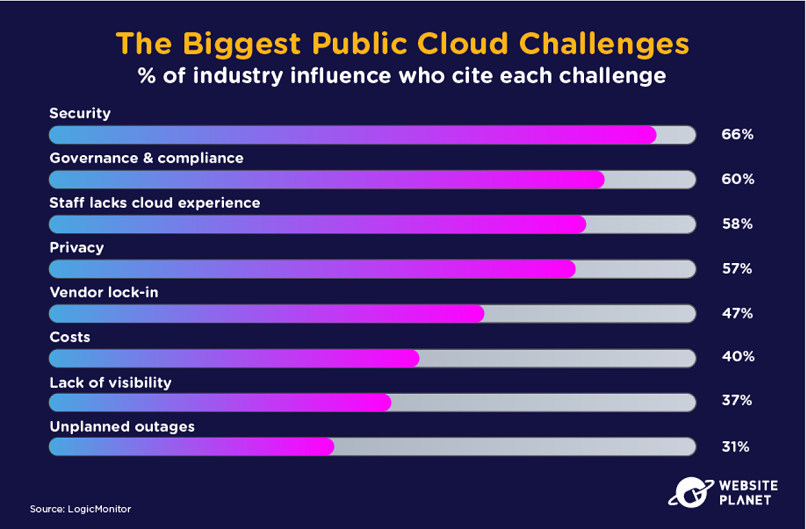
Security is the number one challenge associated with the public cloud, as cited by 66% of industry influencers.
Numerous things can go wrong with the public cloud, from misconfiguration to credential-based attacks, malware, and phishing.
The public cloud looks as though it will continue to grow. Over one-quarter of businesses believe 95% of their critical workloads will operate within the cloud in 5 years.
44. Outside Processors Handle Data
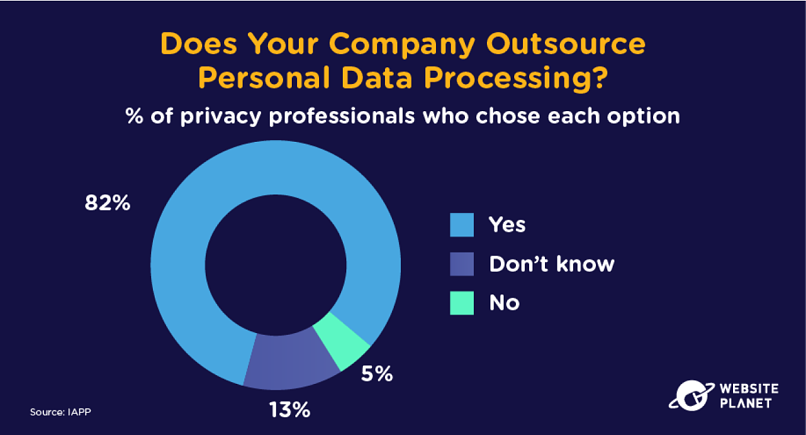
Data processing is typically outsourced to providers that collect, organize and analyze customer data on behalf of another business.
This means the cybersecurity hygiene of the public cloud is often left up to contracted companies. Outsourced services also leave businesses open to supply-chain attacks.
45. Risks Outweigh Benefits
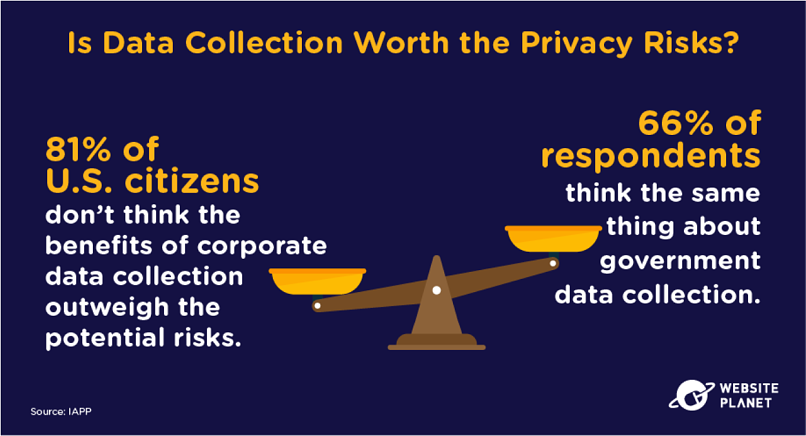
Is it all worthwhile for a few handy auto-fill forms and some personalized recommendations?
Customers overwhelmingly agree that the online comforts associated with big data are not worth the myriad of potential risks. Feelings are less intense when it comes to Government data collection.
Public Data Privacy Perceptions
How aware are people about the security of their data? And what other objections do people have about big data and the current state of data privacy?
46. Big Data Is Worrying

Data privacy and security are a constant worry for many of us. It’s fair to say those worries are justified.
Companies have mishandled customer data on endless occasions over the past few years, and you wouldn’t bet against a few more big data leaks before the year is out.
47. People Don’t Understand Data Privacy

There’s a general lack of understanding about data privacy and data security amongst the general public. Even when data collectors breach our digital rights, a lack of clarity around proper data collection and use often prevents people from taking action.
48. Data Collection Awareness
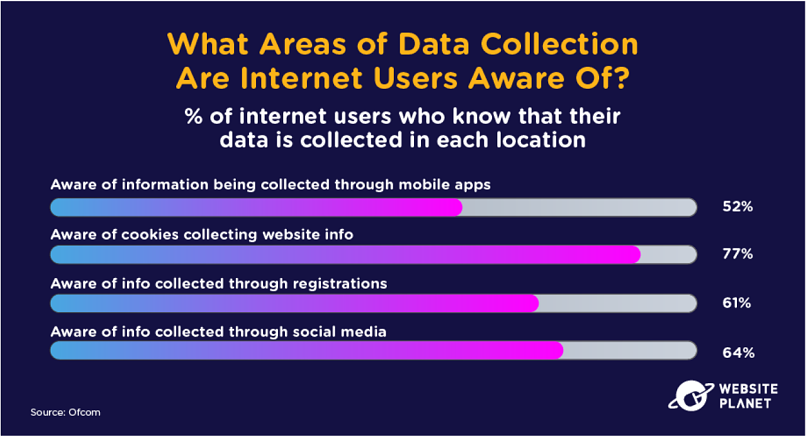
There are loads of different ways companies can collect your data online. 9 out of 10 people are aware of at least one of these methods businesses use to collect our data. However, just 4 out of 10 are aware of all of them.
49. Cybersecurity Technology Awareness
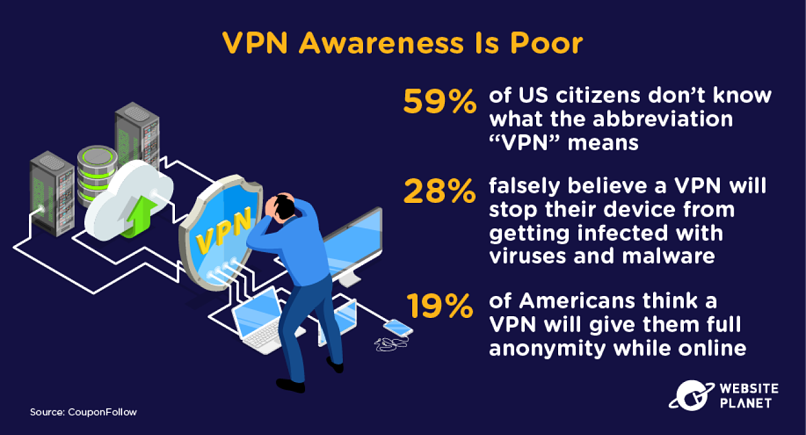
People are not particularly knowledgeable about cybersecurity technology, either. That’s tough, because VPNs and antivirus software can fight back against hackers targeting your personal devices.
50. The Importance of Transparency
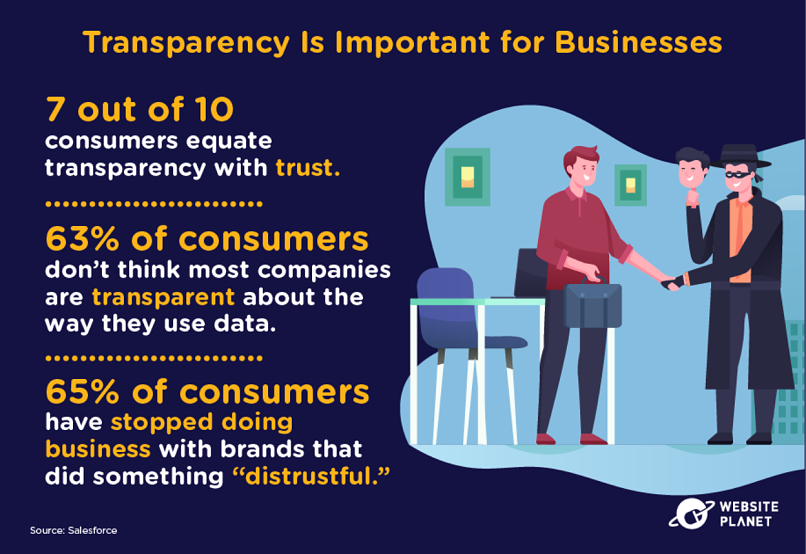
The data collection dynamic between companies and consumers hinges on the word “trust.” Do customers trust that brands will keep their data safe?
It’s essential companies get this right because, according to 73% of consumers, trust in companies means more now than it did in the past. Salesforce found that this trust is waning too. 54% of customers think it’s harder for companies to earn their trust than ever before.
51. Data Collection Is a Mystery

We don’t honestly know what organizations are doing with our data. As the first stat from this section highlights, entities could be doing whatever they want with your data in truth.
Businesses typically use our data for marketing and customer experience purposes. Governments apparently collect our data to help solve crimes. However, judging by this survey, people aren’t entirely convinced.
52. Will Companies Act Responsibly?
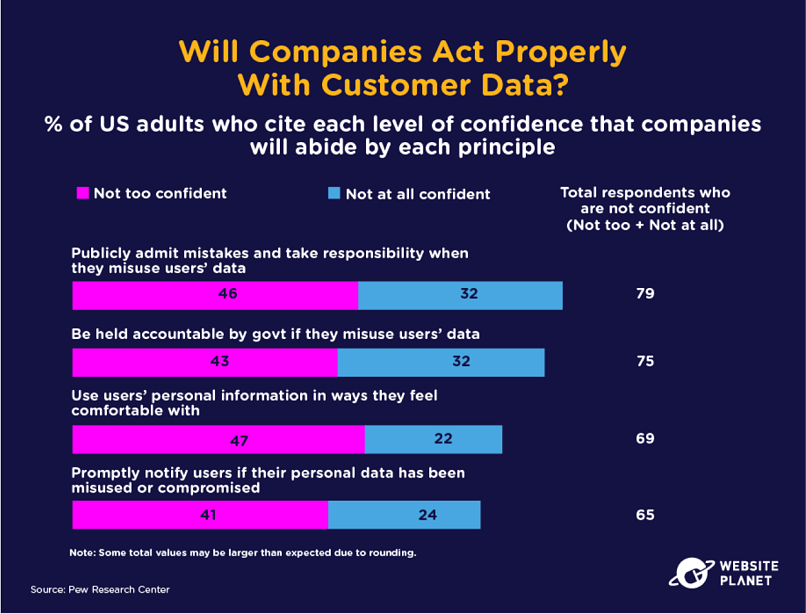
Will companies even admit to misusing or exposing your data? The underreporting of data breaches is a big problem, given the reputational and financial damages breached companies can face.
Most people are skeptical that businesses are prepared to admit their mistakes or be held accountable for their wrongdoings. Unreported data breaches are even more dangerous for the exposed victims.
53. A Surveillance Society

To return to that briefly mentioned theme of “we’re always being tracked,” 72% of people think digital devices are constantly being monitored.
Thoughts of a “surveillance society” have become grounded in evidence ever since the release of the NSA files. Mobile surveillance is now more fact than opinion.
54. COVID-19 Data Concerns
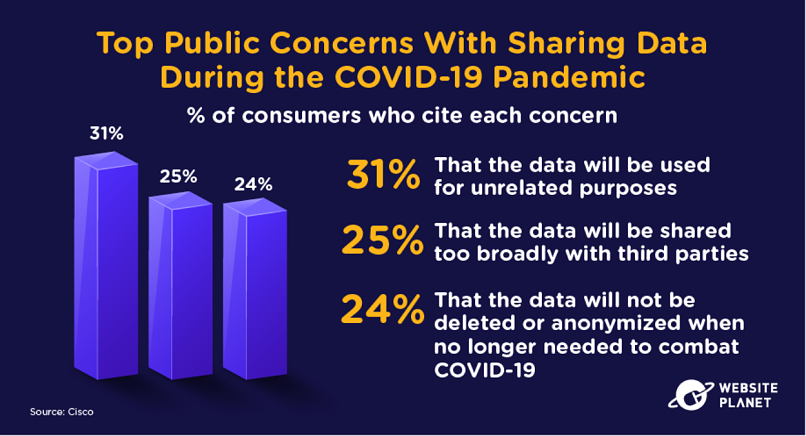
Citizens have shared extra forms of data during the COVID-19 pandemic, whether that’s medical data to receive a vaccine or personal data when signing up for a COVID-19 test.
The general concerns around this data apply to any form of data collection. This perhaps explains why one-half of American adults don’t think online advertisers should store their information.
55. We’ve Already Lost Control

Your biggest data concern should be the fact we’ve “lost control” of our personal information.
Who knows who’s collecting your data, and what for. There are so many background apps, third parties, and forgotten retailers using your data that it’s basically out of your control already.
56. Why Can’t We Protect Our Data Today?
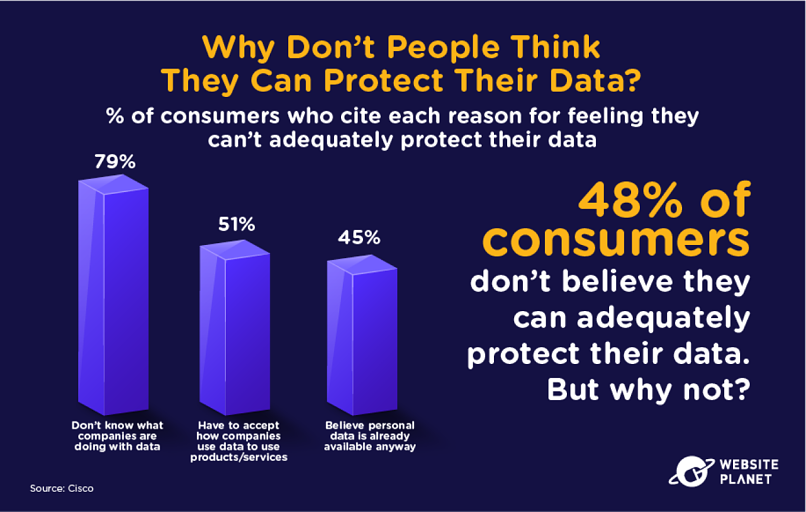
The lack of control over data means users feel that they can’t adequately protect their information in the modern world.
We know users object to the mysterious uses of our data. People also believe they must accept data collection to benefit from services, or because their data is already out there.
57. Should the Government Be Doing More?

Governments should be regulating data collection and use more than they already are.
While laws are already in place, the spate of privacy issues, breaches, and data misuse that we face show that data stores are placing people at risk.
58. Context Matters
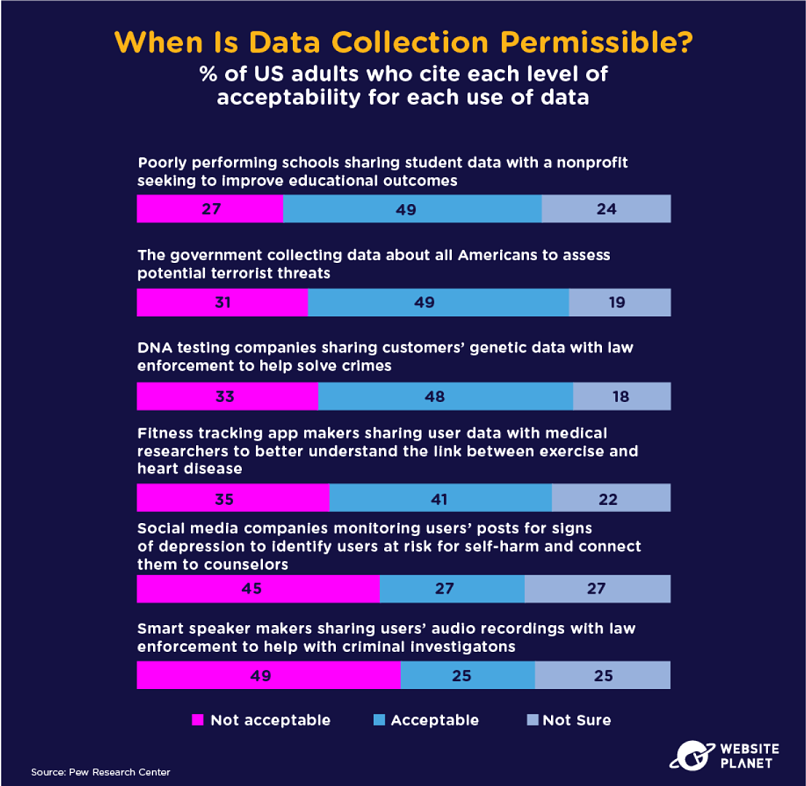
Context matters when companies handle your data. If companies use data to help schools, prevent terrorist attacks, or solve crimes, we’re generally okay with giving it up.
People can’t allow companies to handle their data for every reason under the sun, however. Especially when 41% of global consumers don’t think companies care about their data (Salesforce).
59. People Care About Data Privacy & Security
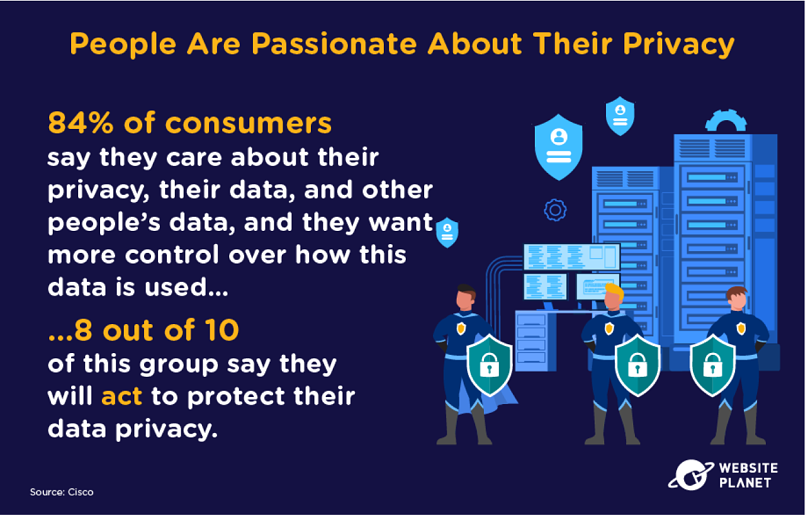
People ultimately care about their privacy and are willing to take action when protecting their online rights.
Only time will tell how far users are willing to go to ensure their digital privacy. Although, we can expect data privacy and security to become a mainstream topic of conversation over the next few years.
Data Privacy Teams & Cybersecurity Procedures
In this section, we’ll look at the companies, departments, and teams tasked with keeping your data private and secure.
How important are data privacy practices? What procedures are teams using? And which emerging security technologies are proving effective in the fight for privacy?
60. Strong Privacy Practices Are Important
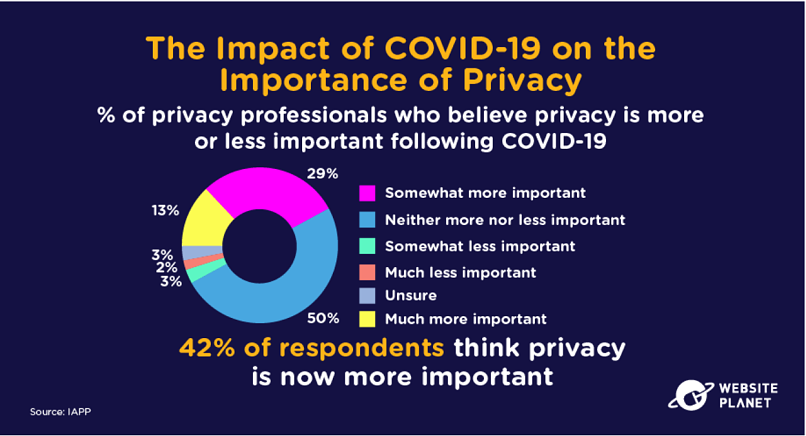
Privacy is important. The increased levels of malicious cyber activity provoked by the COVID-19 pandemic have placed privacy at the forefront of many organizations’ thinking.
42% of organizations believe privacy has become more critical following the onset of COVID-19.
61. Privacy Teams: Top Responsibilities
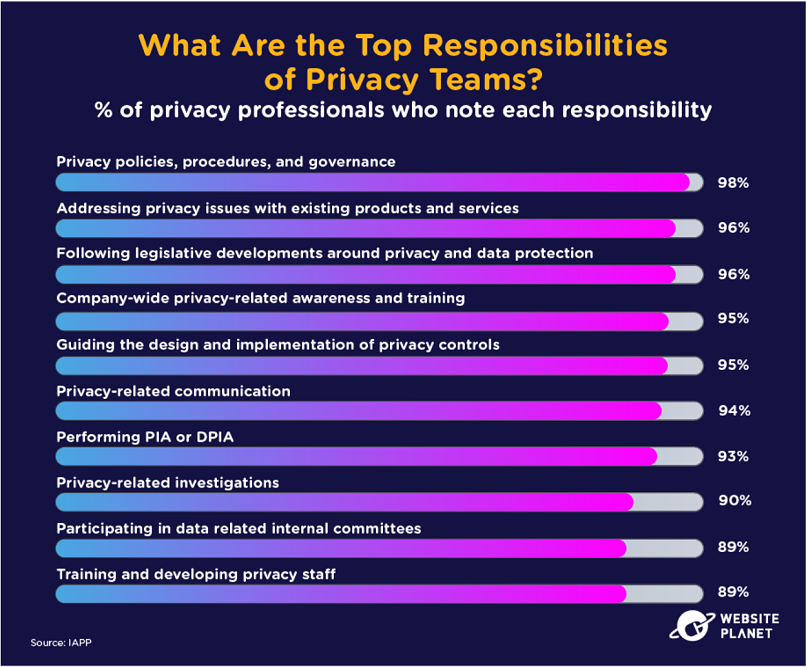
Policy, procedure, and the governance of data privacy are the critical responsibilities of privacy teams.
Elsewhere, incident response is an obligation for 87% of privacy teams, while 81% of teams must maintain GDPR compliance, and 83% of teams must respond to DSARs (data subject access requests).
The least common responsibility was “accelerating digital transformation and digital capabilities” (34%).
62. Privacy Team Priorities
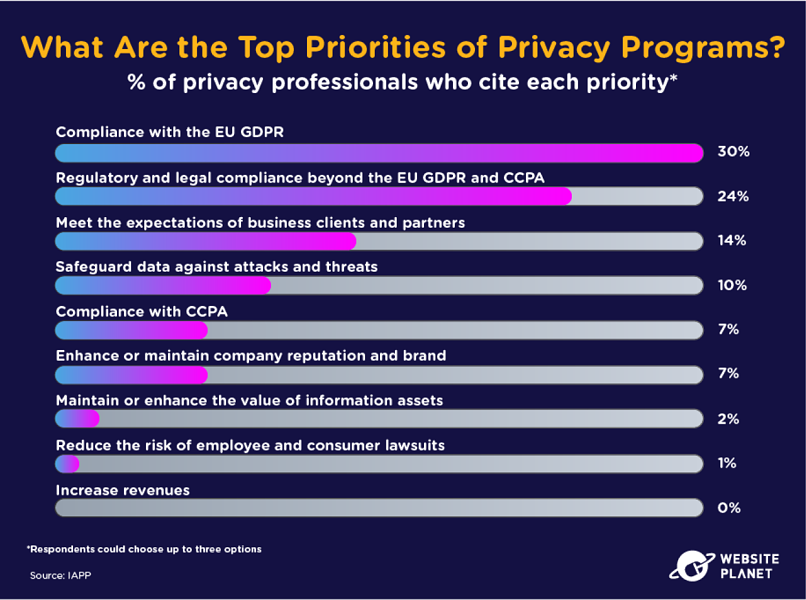
Data protection compliance remains a priority for privacy teams across the globe, whether that’s EU GDPR, CCPA, or otherwise. Failing on this front can be costly.
Compliance is the core function of privacy teams that must keep their organizations in line with regulations. Safeguarding against attacks is only fourth on companies’ list of priorities.
63. COVID-19 Priorities
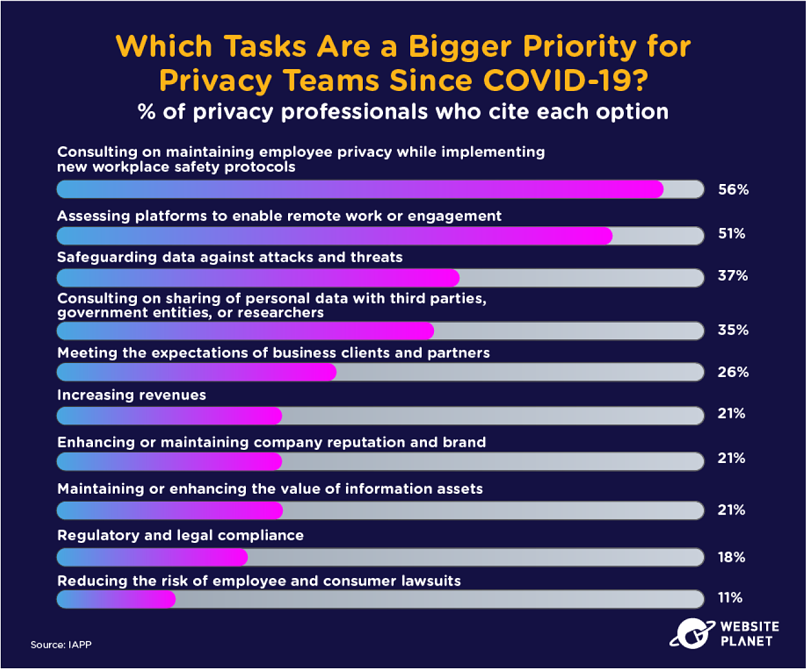
Some tasks have taken on added significance in the wake of COVID-19. Employee privacy and new workplace safety protocols have seen the biggest jump in prioritization. Companies are trying to secure their data as employees work remotely.
64. DPO Adoption
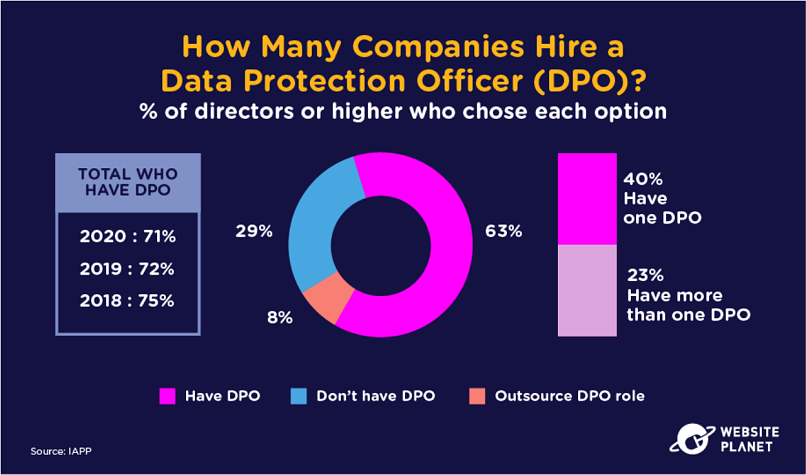
Let’s talk about privacy positions. DPOs are one of the most important leadership roles for compliance in privacy teams.
7 in 10 companies have a DPO. 1 in 10 companies outsource the DPO role while 23% have 2 DPOs.
65. Privacy Spending Doubled in 2020
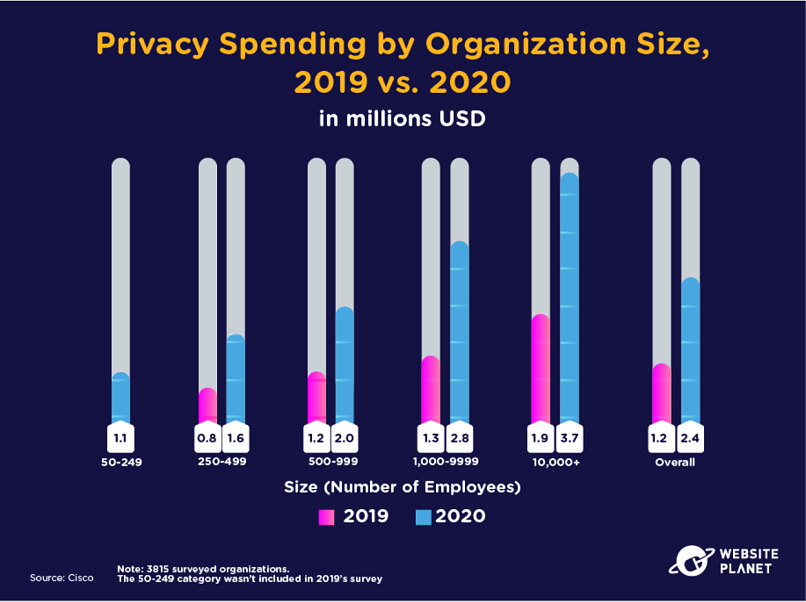
Concurrent with an upward trend in cybersecurity spending, privacy teams spent more money in 2020 than in 2019.
Privacy budgets actually doubled in 2020 to reach $2.4 million on average. Budgets grew under increased pressure from malicious actors.
Meanwhile, 69% of security professionals agree that the enormous costs associated with staying ahead of attackers are unsustainable (Accenture).
66. Digital Transformations Reduce Breach Costs
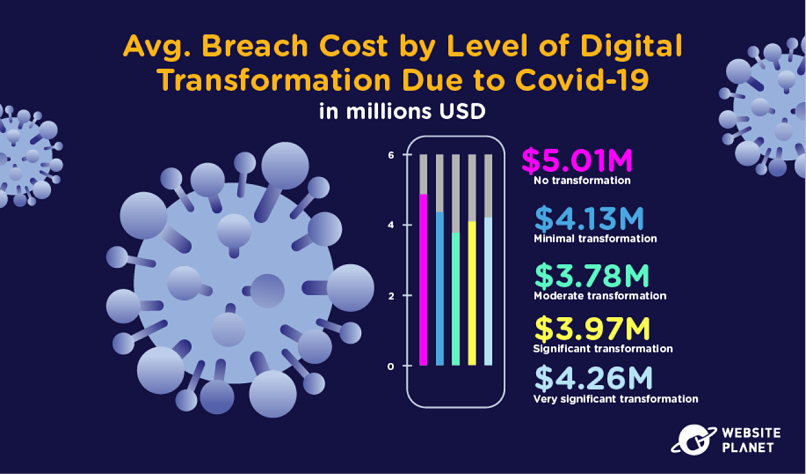
Digital transformation can be defined as adapting and adopting IT to improve business processes. IBM surveyed companies that have undergone digital transformations in response to the pandemic and its related pressures.
Unsurprisingly, companies adopting new technologies at a higher rate generally save more money when they experience a data breach.
67. What Technologies Do Companies Purchase?
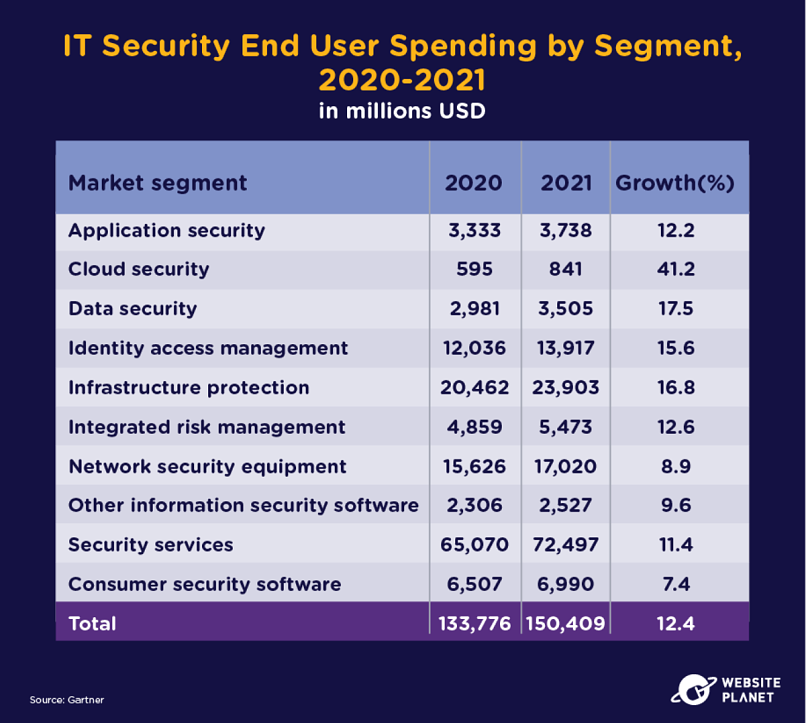
IT security and privacy technologies are experiencing major growth across the board as many companies and individuals ramp up their security spending.
According to Gartner, 61% of chief information officers (CIOs) increased their investment in cybersecurity/information security in 2020. Cloud security solutions saw the biggest growth of any segment in the last year at 41.2%.
68. Privacy Teams: Automation Adoption
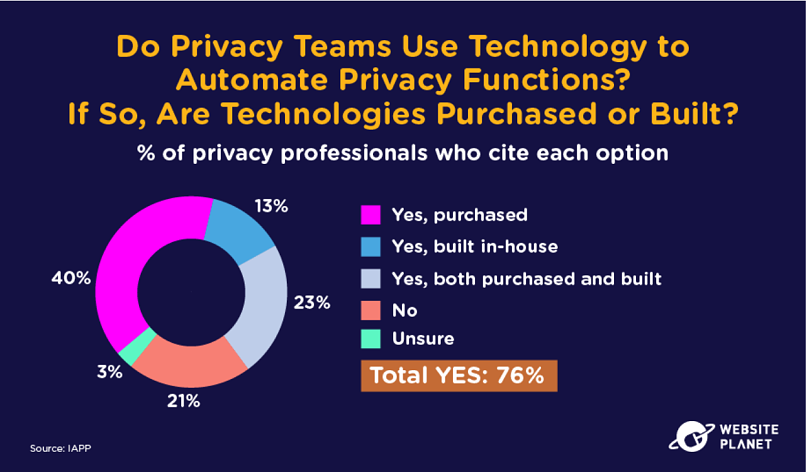
Privacy teams are automating their processes 76% of the time.
Privacy automation is any AI technology that automates privacy-related tasks. This could include responding to data subject access requests (DSARs) and collecting, sorting, and storing consumer data.
Privacy automation reduces the chances of data mishandling and ensures compliance with privacy regulations.
69. Security Teams: Automation Adoption
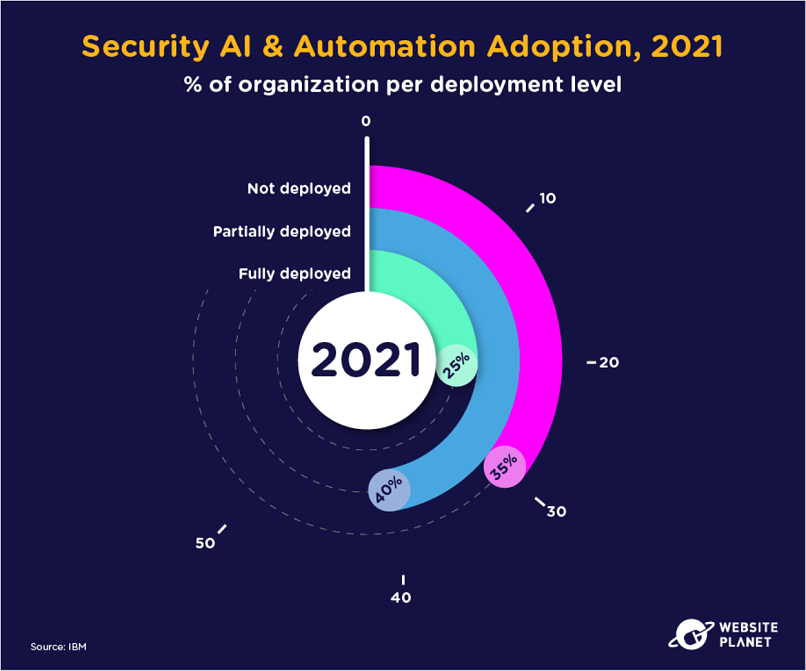
Automation is important for cybersecurity departments too. The majority of companies deployed security automation in 2021.
Security automation is an AI technology that instantly detects and responds to cybersecurity incidents.
70. Automation Reduces Breach Lifecycle & Cost
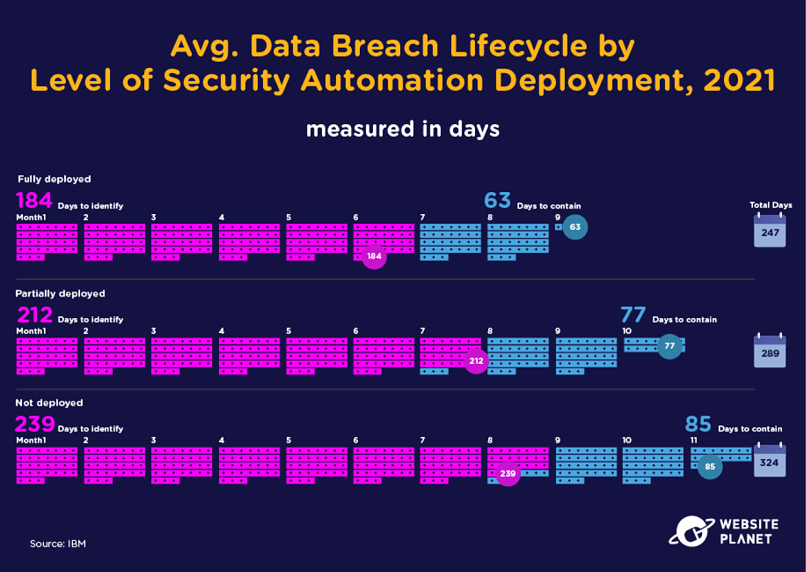
Automation is undoubtedly worthwhile when trying to protect customers’ data. High levels of security automation equate to far shorter breach lifecycles, which means less impact on data handlers and the general public.
Security automation has a financial impact too. Companies that fail to deploy security automation pay 80% more per breach (an additional $3.81 million) than companies that fully deploy security automation.
71. Zero Trust adoption
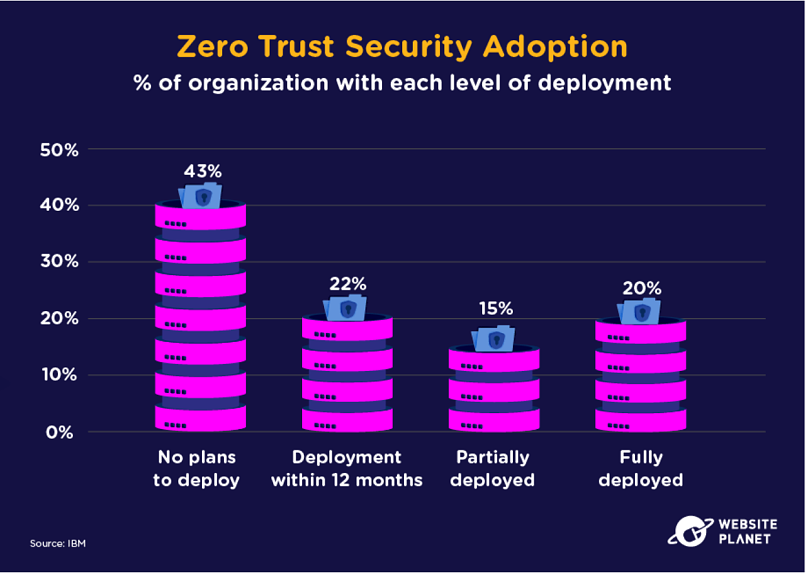
Zero trust security systems work based on the assumption that users and/or networks are already compromised. It’s a different approach to the design and implementation of IT that’s becoming more popular by the day.
72. Zero Trust Reduces Breach Costs
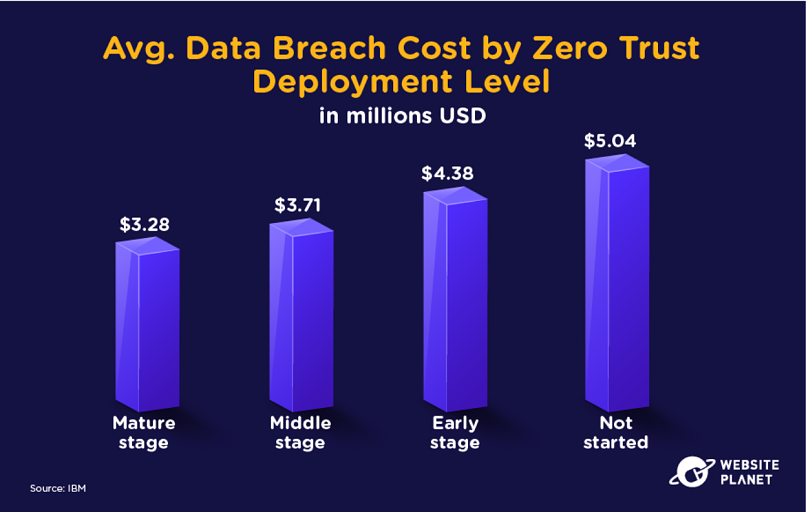
Zero trust security systems certainly succeed in lessening the impact of a data breach. Statistics show that higher levels of zero trust deployment directly correlate with lower data breach costs.
73. Encryption Reduces Breach Impact
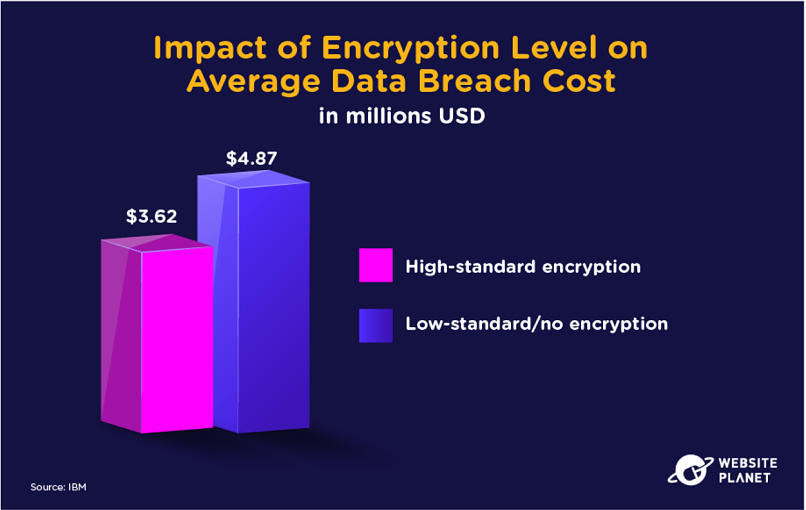
Encryption is one of the major elements of a zero-trust security architecture. Encryption makes information unreadable unless users are properly authenticated.
The research suggests that adopting developed encryption technology (at least 256 AES encryption) can massively reduce the cost and impact of a data breach.
74. Incidents Response Is Essential for Teams
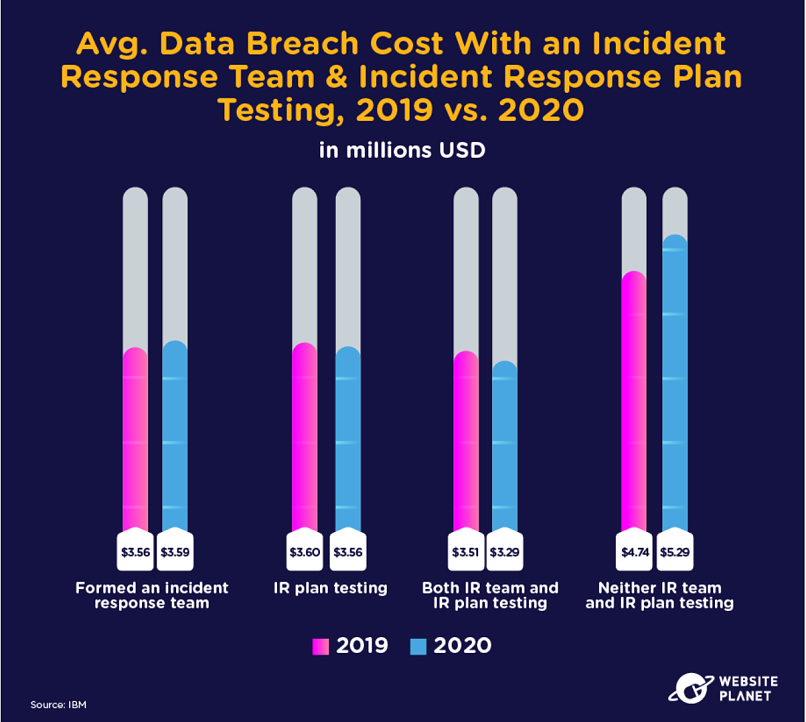
Every company should have an incident response plan in place.
Companies might have a dedicated incident response team, or the responsibility could fall to privacy teams. Either way, extensive IR planning and testing will reduce the costs of a corporate data breach by $2 million.
75. HTTPS Protocol Secures Website Domains
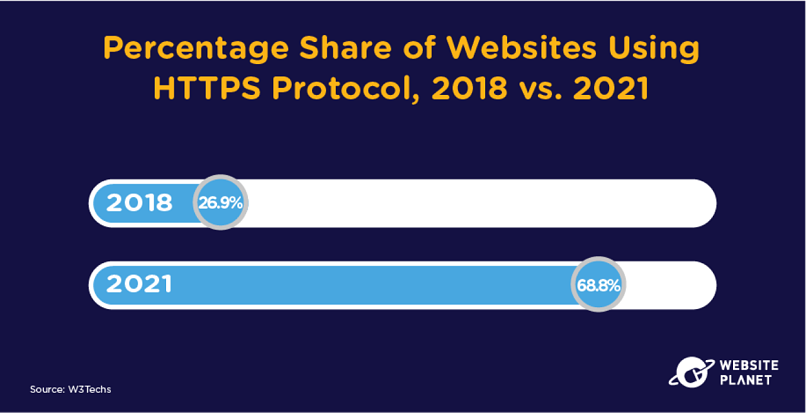
More and more businesses are adopting HTTPS protocol on their websites and web applications.
HTTPS makes websites safer by adding an extra layer of encryption to secure site communications. HTTPS can prevent man-in-the-middle attacks, phishing attacks, and malware attacks.
76. The Impact of Hybrid Cloud Servers
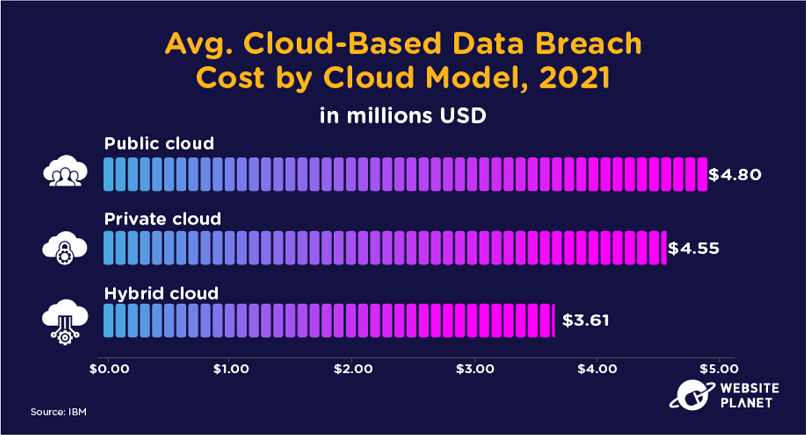
Many companies have been transitioning to the public cloud over the last few years. However, research suggests a mixture of public and private cloud solutions could mitigate the impact of data breaches.
77. Privacy Spending Benefits
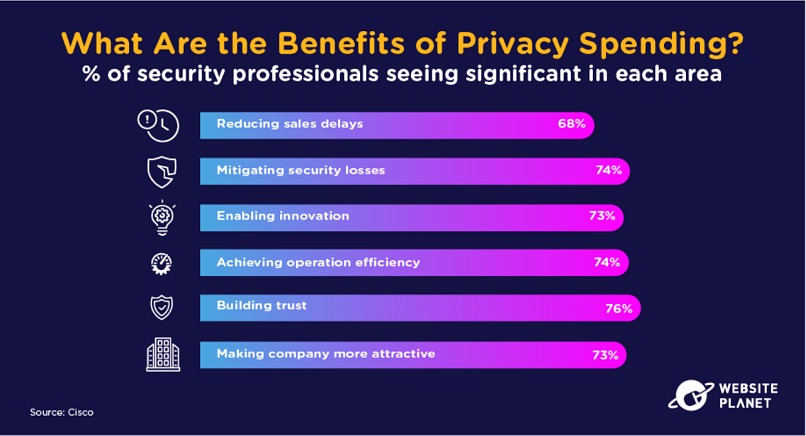
Of course, there are loads of monetary benefits when investing in cybersecurity procedures. Investing in data privacy can arguably see even bigger gains.
Two-thirds of businesses claim to get trade benefits from data privacy procedures.
That’s why data privacy has such a great ROI; 35% of businesses report 2X ROI from their privacy investments.
Personal Precautions & Protecting Devices
In this section, we’ll take a look at the state of personal protection.
Are we protecting our own data enough? And what privacy precautions and cybersecurity solutions can users implement to protect their data and devices?
78. Who’s Responsible for Protecting Data?
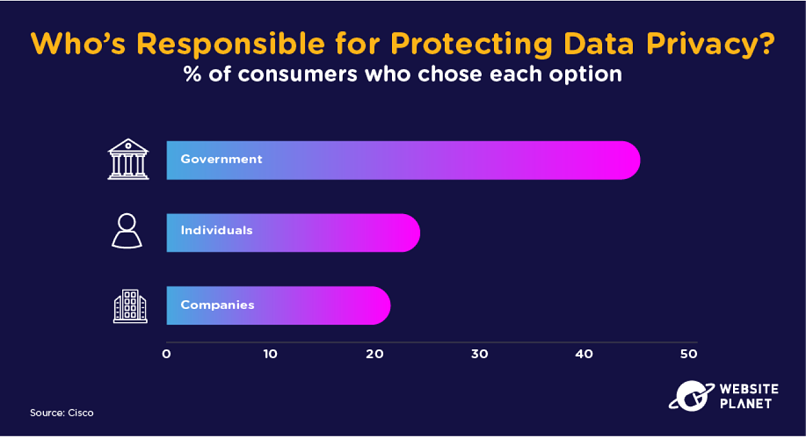
45% of consumers believe the government is solely responsible for protecting data privacy.
Just 24% believe the responsibility lies on the shoulders of individuals, and 21% believe companies are responsible. In truth, protecting data is everyone’s responsibility…
79. People Don’t Protect Their Own Data Enough

Governments need to do more to educate citizens about their online privacy, and perhaps some companies need to stop exploiting vulnerable users. Still, people should be proactive about their own privacy too.
It’s all well and good complaining about the state of data privacy. More people need to learn about data privacy and security to make the correct decisions when needed.
80. Privacy Actives Abandon Companies
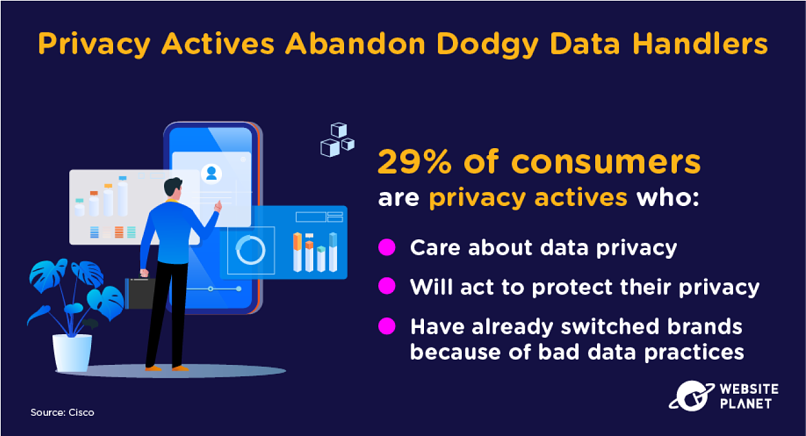
“Privacy actives” are, as the name suggests, active about their data privacy and security.
According to Cisco, 29% of customers are already privacy activists. These people really care about their data, are willing to act to protect it, and have already switched brands over their data policies. 42% of all consumers in Cisco’s survey have switched brands to protect their data.
81. Who Do Actives Abandon?
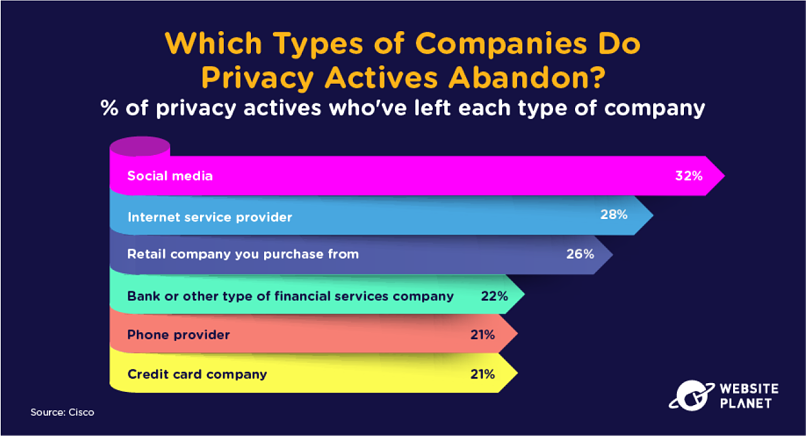
Privacy actives are abandoning social media companies and ISPs more often than others.
Social media sites and applications have some of the most questionable data policies out there, so this is no real surprise.
82. What Personal Precautions Do Users Take?
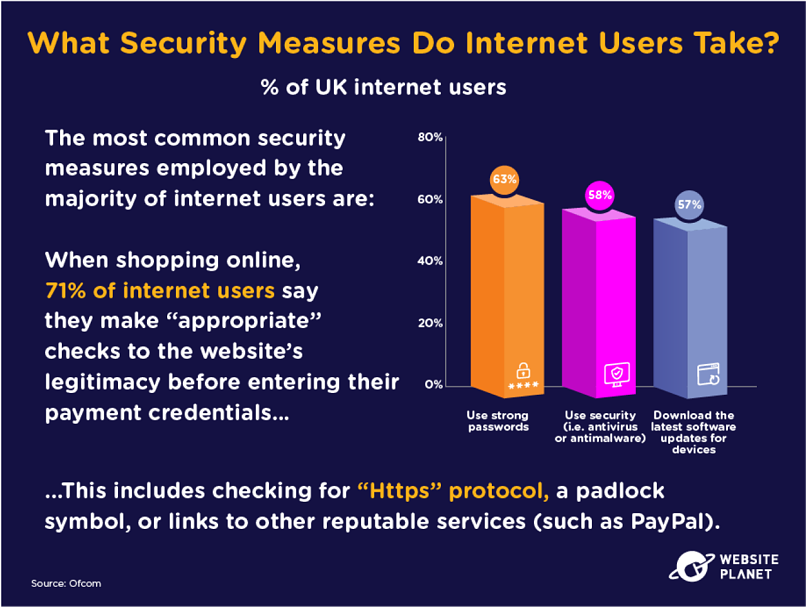
90% of internet users in Ofcom’s survey take (or live with someone who takes) security measures to protect their online privacy.
Strong passwords, antivirus technology, and software updates are all utilized by internet users, while eCommerce shoppers will often check through a website before making a purchase.
83. Why Don’t People Read Privacy Policies?
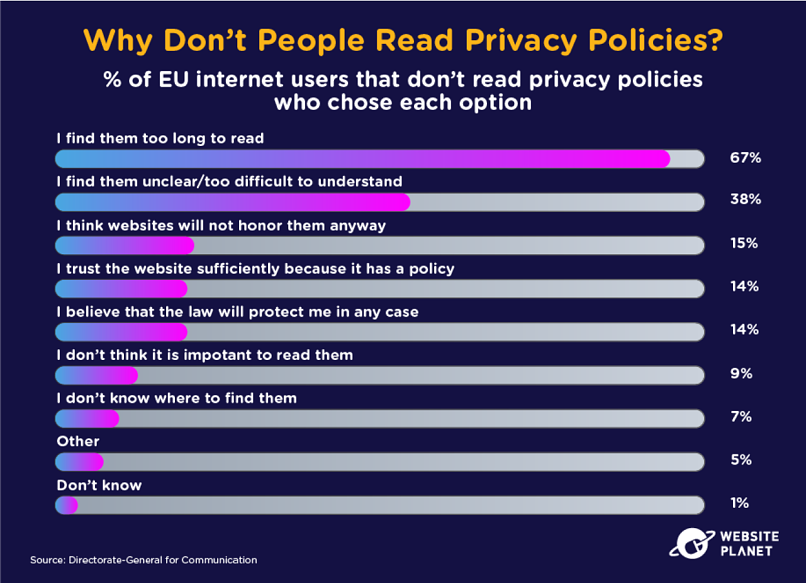
A Pew Research Center survey found that 36% of American internet users never read privacy policies before agreeing. That’s compared to 83% of privacy actives who read privacy policies (Cisco).
We should all be checking privacy policies and terms and conditions before we buy a product or use a service. Policies are often too long and convoluted, which is a big reason so many people can’t be bothered.
84. How Do People Avoid Tracking?
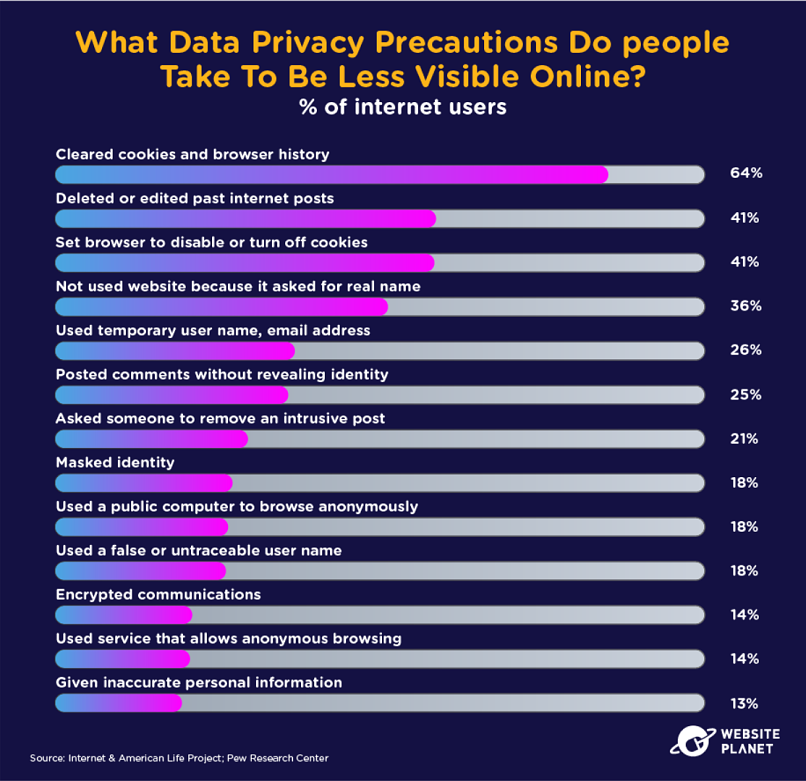
There are certain precautions users take to avoid being tracked and reduce their online footprint’s visibility.
Clearing cookies and browsing data is the number one way to avoid online tracking, while editing past posts is also an effective way to remain anonymous.
85. What Social Media Precautions Do Users Take?
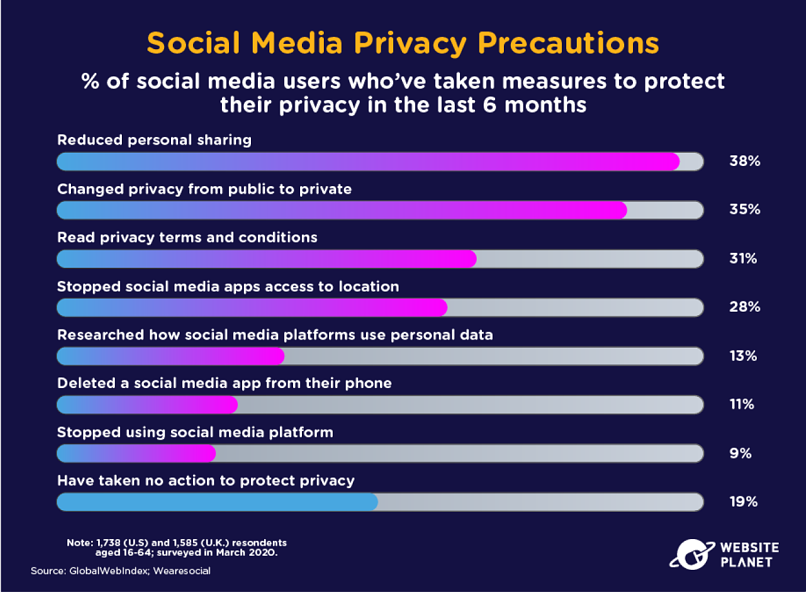
According to DuckDuckGo, 79% of people have either adjusted their privacy settings on social media accounts or reduced their overall use of social media.
The GlobalWebIndex researched the specific precautions social media users are taking, with 38% of people simply reducing the amount of information they share.
86. Protecting Child Data

It makes sense that parents are monitoring their children online. Who knows what privacy problems kids could experience without regulation?
The security of childrens’ data is now a fresh concern with so many targeted advertisements, questionable privacy policies, Ts & Cs, cookies, and cybersecurity threats to navigate online.
87. Child Data Precautions
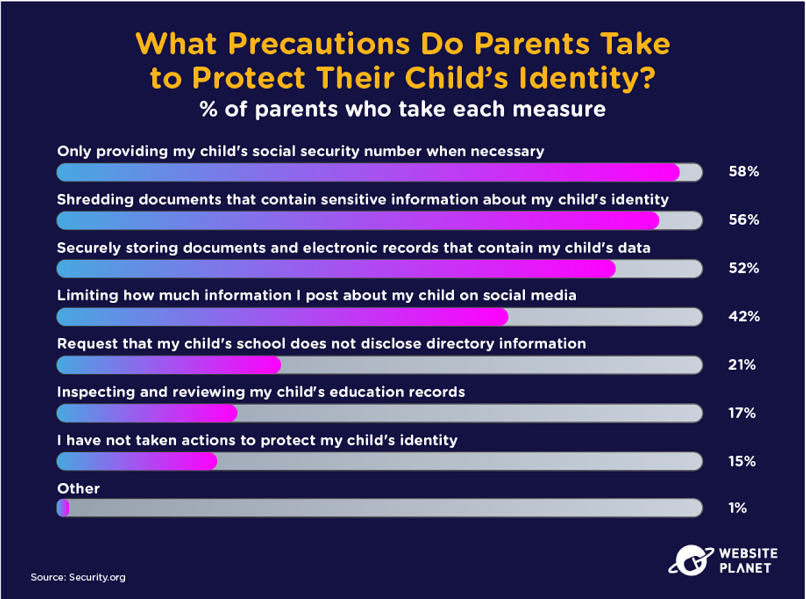
Parents should buy a product or use important methods to keep their child’s identity secure, including shredding documents, limiting social media posts, and securely storing documents. Now that’s parenting done right!
88. Why Use Antivirus Software?
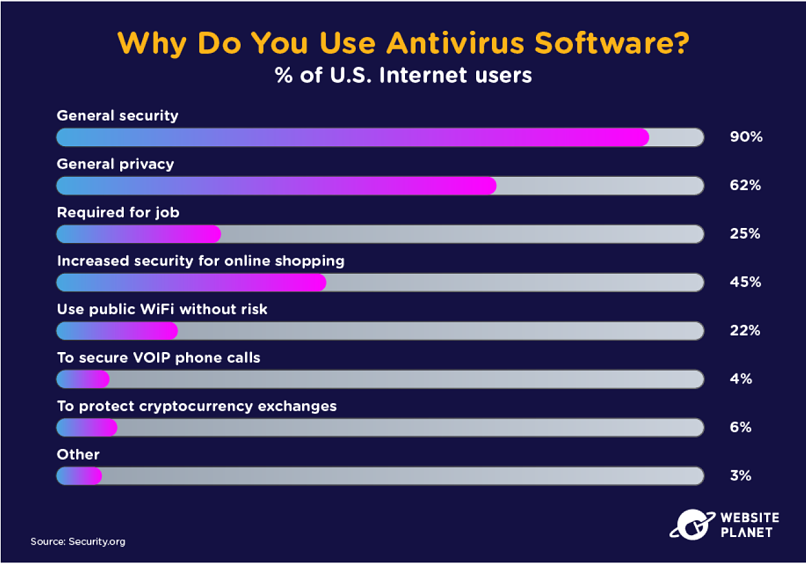
82% of US internet-connected households use antivirus software. Privacy and security are the two biggest reasons for antivirus adoption.
Antivirus software is excellent for keeping your data protected. 98% of users think antivirus software is “somewhat” or “very” effective. In fact, antivirus programs across the globe detect 350,000 viruses every day.
89. VPN Adoption
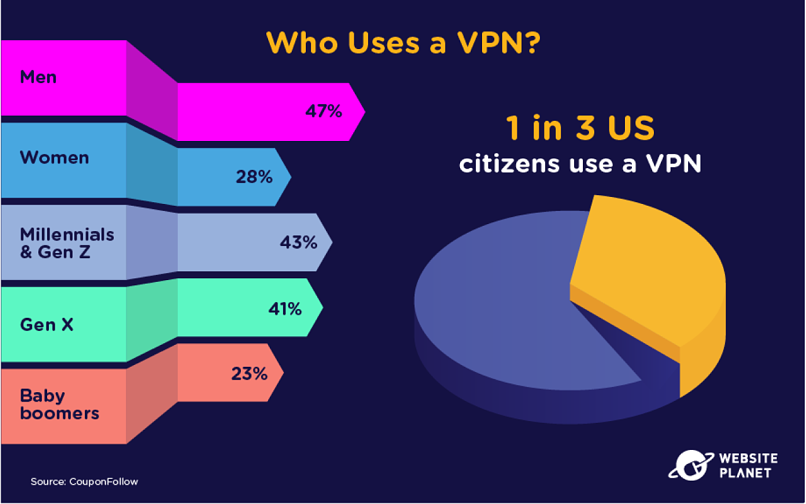
35% of Americans use a VPN, and VPN use is more common amongst male millennials and GenZers.
VPNs were first introduced commercially way back in 1996. They’re now a popular measure employed by internet users who want to encrypt their internet traffic and search anonymously.
90. Why Use a VPN?
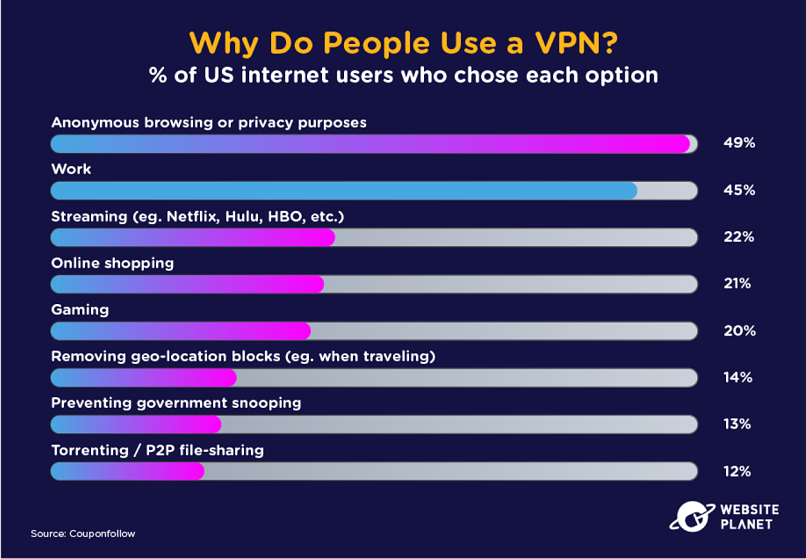
What are the benefits of using a VPN? Data privacy sits at the top of the agenda.
Users can also shop securely, share files without worry, and surf the internet free from government surveillance. No wonder 96% of VPN users in a Security.org survey rate the software as “somewhat” or “very” effective.
Final Section: Data Protection Legislation & Compliance
In this final section, we’re diving into the current state data privacy legislation around the world.
Which nations have data protection laws? Which countries don’t? What‘s the impact of compliance and failure? And how costly are the biggest data protection fines?
91. The Data Protection Map
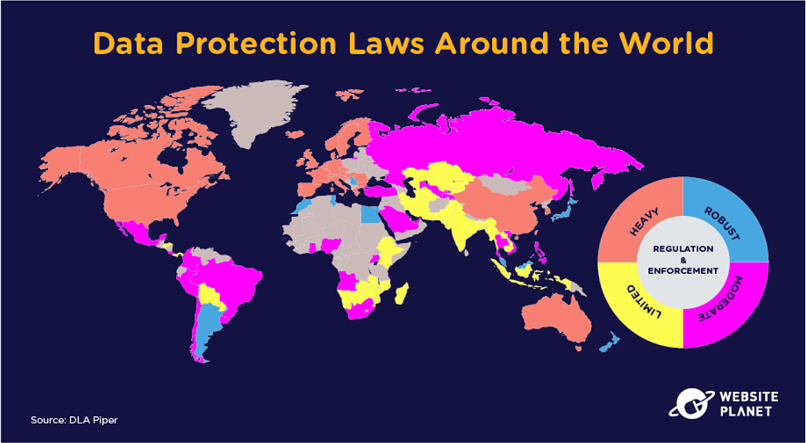
DLA Piper looked at the regions with the most stringent data protection regulations.
North America, Europe, China, and Australia are the 4 regions deemed to have the best data protection regulations and effective implementation of data laws. Data protection laws are non-existent in some other nations.
92. How Many Countries Have Data Protection Laws?
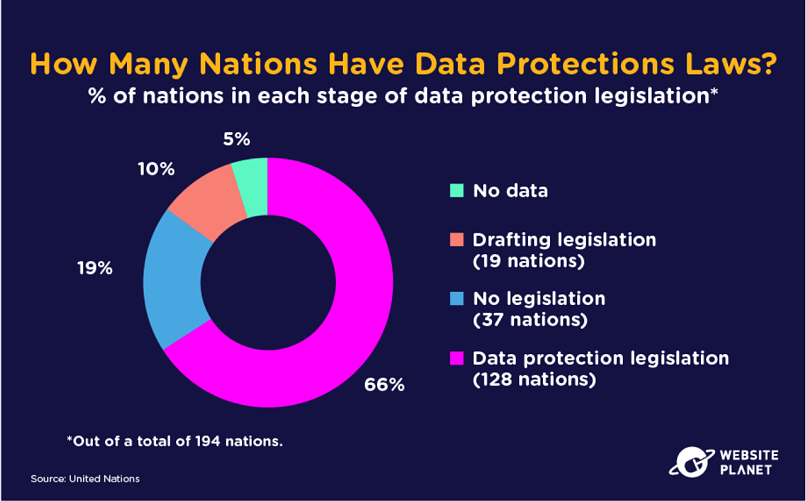
Around 66% of countries currently have data protection legislation in place. A massive 19% of nations don’t have any legislation. Most of these countries are in Africa, including Chad, Libya, Sudan, and Egypt.
93. GDPR Compliance
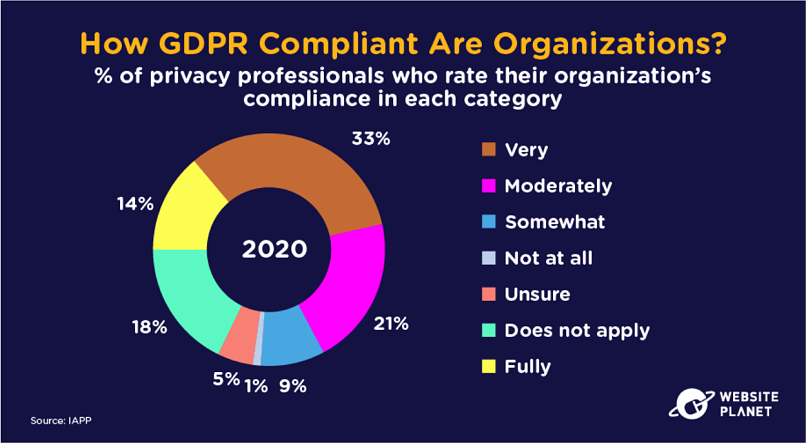
Any company that conducts business with EU customers, wherever that business is located, must comply with GDPR: the world’s most stringent and developed data protection regulations.
77% of global businesses surveyed by the IPAA are compliant with GDPR to some degree. That’s so important in today’s age of globalization.
94. The Upsides of GDPR Compliance
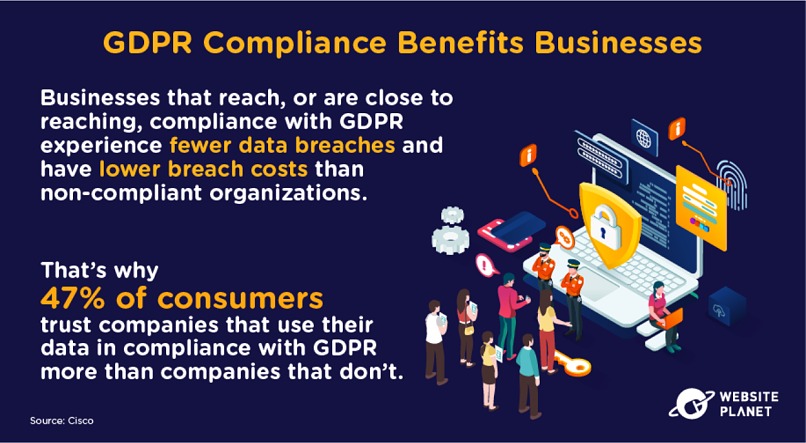
Compliance with GDPR will reduce the magnitude, severity, and frequency of data breaches that an organization suffers.
Customers are more likely to trust businesses that follow GDPR for this very reason, which is why GDPR compliance can eventually return revenue.
95. Who’s Hot on GDPR?
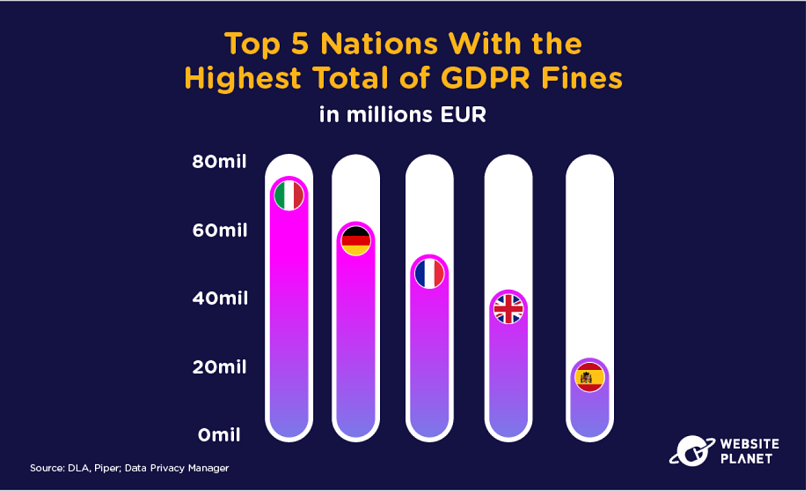
Italy dishes out more GDPR fines than any other European nation. Germany has issued over €60 million of fines since the implementation of GDPR in 2018, while France has issued over €50 million in fines.
The UK has left the EU but retains its own version of GDPR. The UK has issued just over €40 million in fines.
96. The Biggest GDPR Fines

The GDPR has been criticized at times for the inadequate value of its sanctions. The GDPR’s focus is on compliance and instigating proper data protection practices, although GDPR still lags behind US regulators in the quality of its enforcement.
There are signs that GDPR will be enforced more effectively in the future. Luxembourg recently handed Amazon a huge €746 million ($885 million) GDPR fine, which eclipses any of the above sanctions. Amazon has appealed the decision, so we can’t add it to our list just yet.
97. The Biggest US Data Breach Fines & Settlements
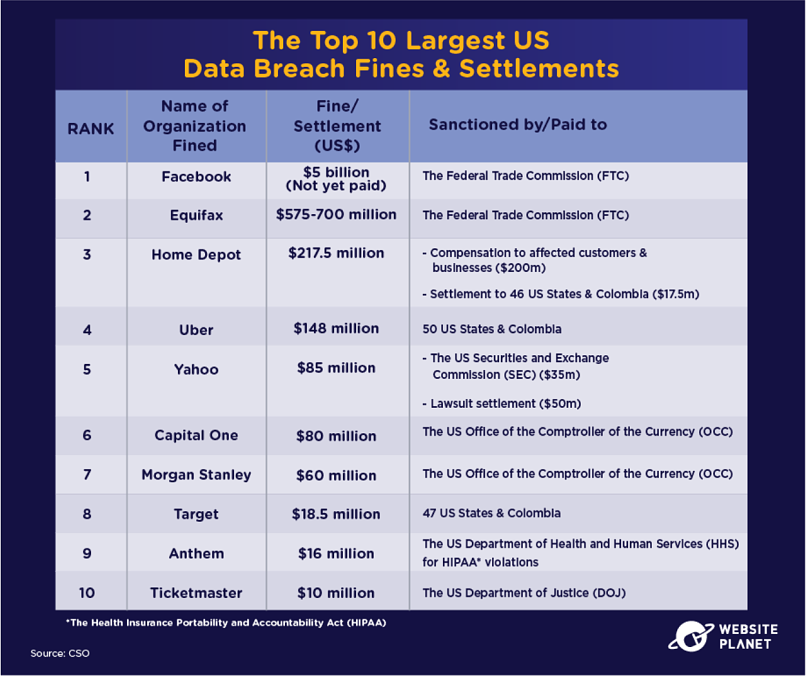
There are several different regulatory organizations in the USA, and these entities fine institutions for data breaches in their respective fields.
The HIPAA deals with healthcare breaches, while the US Securities and Exchange Commission (SEC), the Federal Trade Commission (FTC), the Department of Justice (DOJ), and the Office of the Comptroller of the Currency (OCC) are all known to hand out hefty fines as well.
98. CCPA Compliance
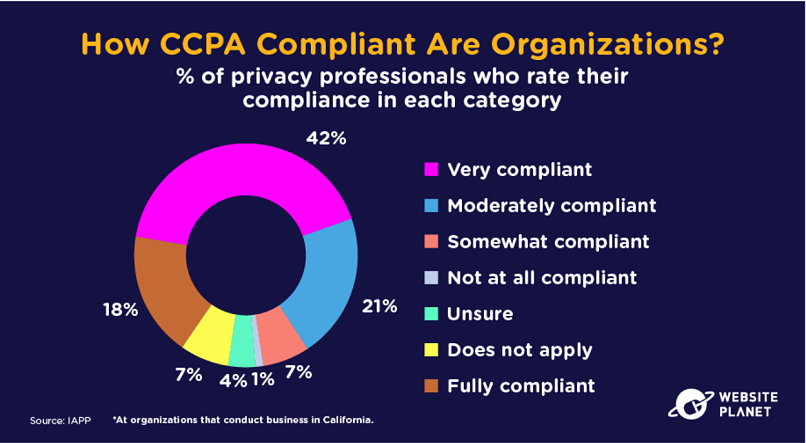
There are no federal-level data protection laws in America. The FTC may get involved in investigations, although, on a state level, 47 US States don’t have consumer data protection laws in place.
CCPA is California’s new data protection law, which is based on the EU’s GDPR. While other US organizations (such as the FTC) focus on sanctions, the CCPA follows a more European emphasis on compliance.
99. Regulators Look Kindly on Reporters

Companies should certainly report a data breach no matter the jurisdiction they’re in. Regulators look kindly upon companies that report data breaches. So much so, that only 2% of these companies are fined.
100. The Impact of Compliance Failures
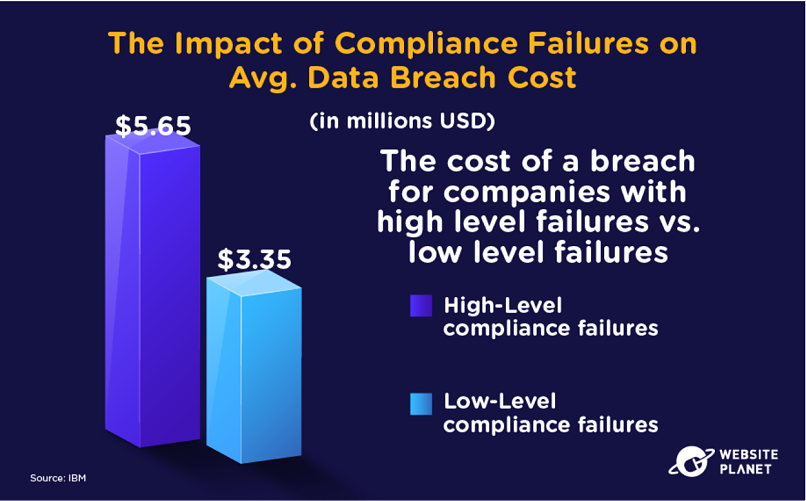
Organizations want to avoid as many compliance failures as possible. Not only can compliance failures land data handlers with extra penalties, but they can drive up the damages of a data breach too.
101. Privacy Pays
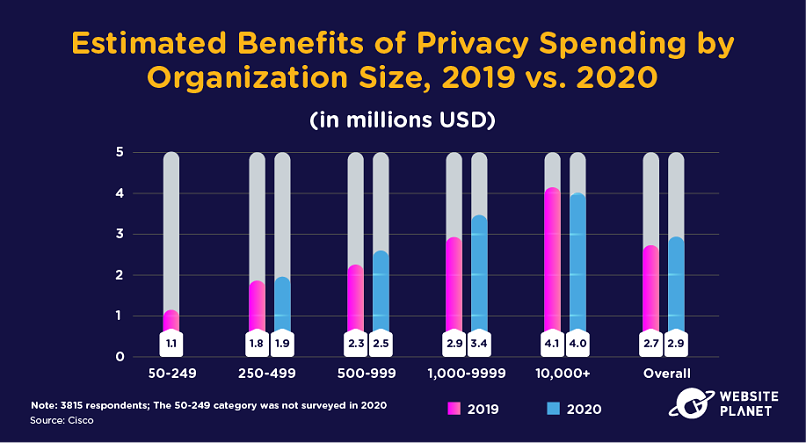
Despite the huge costs of compliance, companies can make a tidy profit when preparing for data protection regulations.
Data privacy compliance is essential given the lower risk of data breaches and subsequent fines, yet many companies are also making money from the trade benefits of compliance.
According to Salesforce, 84% of global consumers are more loyal to businesses with robust security systems in place.
102. The Impact of Privacy Around the World
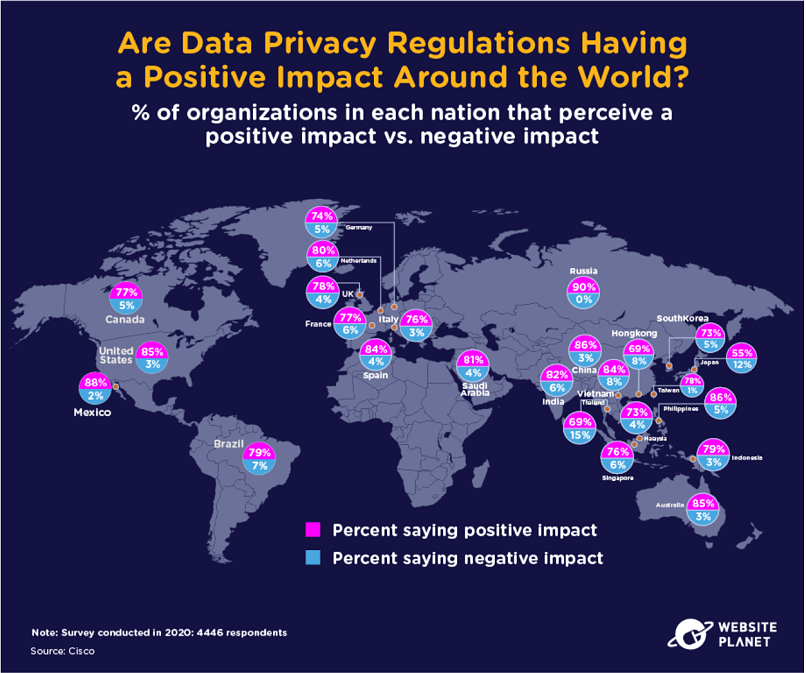
Privacy laws are seen as a hugely positive and effective step forward for data privacy around the world. Across all nations in Cisco’s survey, 79% of organizations said that privacy laws had a positive impact, and just 5% cited privacy regulations as a negative.
How to Protect Your Data
A few parting tips to help you keep your data secure when surfing the internet.
Create Strong Passwords
You need to make sure you create super secure passwords across all of your accounts. That means creating passwords that contain a combination of upper and lowercase letters, numbers, and symbols.
Avoid using common phrases and names and using personal dates and information (such as your birthdate). Have separate passwords for each account too. That way, cybercriminals can’t compromise all of your accounts should they gain access to one.
Use Cybersecurity Software
Your data is in far greater danger if you’re not already using some form of cybersecurity software. It’s a no-brainer. Antivirus, antimalware, and antispyware programs can be purchased for a small fee and could save you no end of time and money further down the line. Most home device cybersecurity software will protect you against all manner of malware varieties too.
Elsewhere, encrypting the data on your device is a good idea. This will stop bad actors from extracting your data should you lose a device. Virtual private networks (VPNs) are great as well. VPNs encrypt your internet traffic to create a secure connection to the internet.
Update Device Software
Make sure you update your device software regularly. As mentioned, outdated operating systems, web browsers, and apps could contain crippling vulnerabilities that provide access to your data. These vulnerabilities are normally patched, so keep an eye out for any fresh updates!
Avoid Certain Tasks on Public WiFi
Public WiFi is often unencrypted and, as such, can allow hackers to snoop on your activities and gather your data. Avoid any tasks that involve your personal data whenever you’re connected to free WiFi. That means no eCommerce purchases while you’re in the local cafe!
Be Careful What (& Where) You Click
Bad actors will try to phish your data with malicious links on messages, websites, or through Trojan malware hidden in apps.
Third-party app stores are a popular place for hackers to hide malware, while users should look out for messages from unknown sources asking for you to disclose information or carry out some kind of action. Only click a link anywhere online if you can trust the source 100%.
Clear Cookies & Edit Tracking Permissions
You can clear your cookies in the settings of your browser every few months, and it’s worthwhile blocking all third-party cookies in your settings too. Websites use cookies to track your online behaviors, and some of these cookies track you for an unnecessarily long time. Clearing and blocking cookies will reduce the amount of data companies collect on you, which will reduce the chances of your data being stolen in a breach.
Edit Privacy Settings on Social Media
You should change your privacy settings across social media accounts so that only trusted people/friends can see your public posts and personal information. This will mean malicious actors won’t be able to gather your data when viewing your page.
Read Privacy Policies/Terms & Conditions
Just because a company has a privacy policy doesn’t mean it’s a good one. Companies may be collecting a lot more of your personal data than you think, and they could be selling your information to third parties.
Read privacy policies and Ts and Cs before you agree. That way, you can decide whether you’re comfortable with a company’s data collection and sharing practices before giving up your information in a legally binding contract.
The Bottom Line
The internet is a place full of potential data privacy dangers and security threats. Thankfully, a number of these risks can be mitigated through proper online practices and cybersecurity hygiene.
Moreover, data privacy is a developing field. The security of our data will likely improve as people continue to realize their online rights and companies are better regulated by governing bodies. We’re sure data privacy and security will get up to speed soon enough!
In the meantime, you can navigate a minefield of potential slip-ups by implementing a few of the data protection tips mentioned above. Thanks for reading!
About the Author

- Tom Read
- Cybersecurity Researcher
Tom is a technology writer and researcher. He’s a strong advocate for digital rights, online privacy, and the value of ethical hacking