Report: Educational Platform Exposes Private Data of Over 1 Million Students across North America
Source:https://www.vpnmentor.com/blog/report-oneclass-breach/

Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach belonging to the e-Learning platform OneClass.
OneClass is a remote learning platform that provides study guides and educational assistance materials to millions of students across North America. At a time when students are forced to study from home, feeling isolated and stressed, such resources are more valuable and popular than ever.
By not securing its users’ data, OneClass created a goldmine for criminal hackers, jeopardizing the privacy and security of over a million young people and their families.
Data Breach Summary
| Company | OneClass |
| Headquarters | Toronto, Canada |
| Industry | e-Learning |
| Size of data in gigabytes | 27 GB |
| Suspected no. of records | 8,972,251 |
| No. of people exposed | 1,000,000+ |
| Date range/timeline | Prior to 2019 |
| Geographical scope | North America |
| Types of data exposed | PII data; educational data |
| Potential impact | Phishing, fraud |
| Data storage format | Elasticsearch, hosted on AWS |
Company Profile
OneClass was founded in 2010 and is currently based in Toronto, Canada.
The company has built an educational platform that “allows university students to collaborate and share study resources from self-created lecture notes to study guides.”
OneClass claims to have helped over 600,000 students with their academic studies, although the real number is probably much higher. We estimate it had incorrectly stored the data of over one million people, including people whose membership had been ‘rejected’ from the platform.
While some of the study material on OneClass is free, students’ most valuable resources are only available through a paid membership.
Timeline of Discovery and Owner Reaction
Sometimes, the extent of a data breach and the owner of the data is obvious, and the issue quickly resolved. But rare are these times. Most often, we need days of investigation before understanding what’s at stake or who’s leaking the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research, or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, once we confirmed OneClass as the owner of the database, we disclosed our findings to the company and outlined the nature of the breach.
In response, OneClass immediately secured the database but claimed that it was a test server, and any data stored within had no relation to real individuals.
However, during our investigation, we had used publicly available information to verify a small sample of records in the database. Taking the PII data from numerous records, we found the social profiles of lecturers and other users on various platforms that matched the records in OneClass’s database.
Based on this, we doubt the veracity of OneClass’s claim and stand by our assessment.
We once again reached out to OneClass to show further proof of our findings. However, we received no further replies from the company.
- Date discovered: 20th May 2020
- Date vendors contacted: 25th May 2020
- Date of Response: 26th May 2020
- Date of Action: 26th May 2020
Example of Entries in the Database
On its website, OneClass states that it “applies necessary physical, technological, and administrative measures to protect Personal Data at the level appropriate to its sensitivity… under the highest data security standards.”
Based on our team’s discovery, however, this was not the case.
The exposed database was built on an Elasticsearch framework and hosted on Amazon Web Services (AWS), but left completely unsecured.
It contained over 27 GB of data, totaling 8.9 million records, and exposed over 1 million individual OneClass users. The database contained different indices, each with different types of records related to students using the platform, those who had been rejected from joining, many university professors, and more.
These records contained different forms of Personally Identifiable Information (PII) data for every user exposed, including:
- Full names
- Email addresses (some masked, many viewable)
- Schools and universities attended
- Phone numbers
- School/University course enrollment details
- OneClass account details
It’s also possible that some of the data belongs to minors, as OneClass includes resources for high school students and accepts users from 13 years old and above.
In the following screenshots, entries from two students provide a sample of the PII exposed in OneClass’s records:
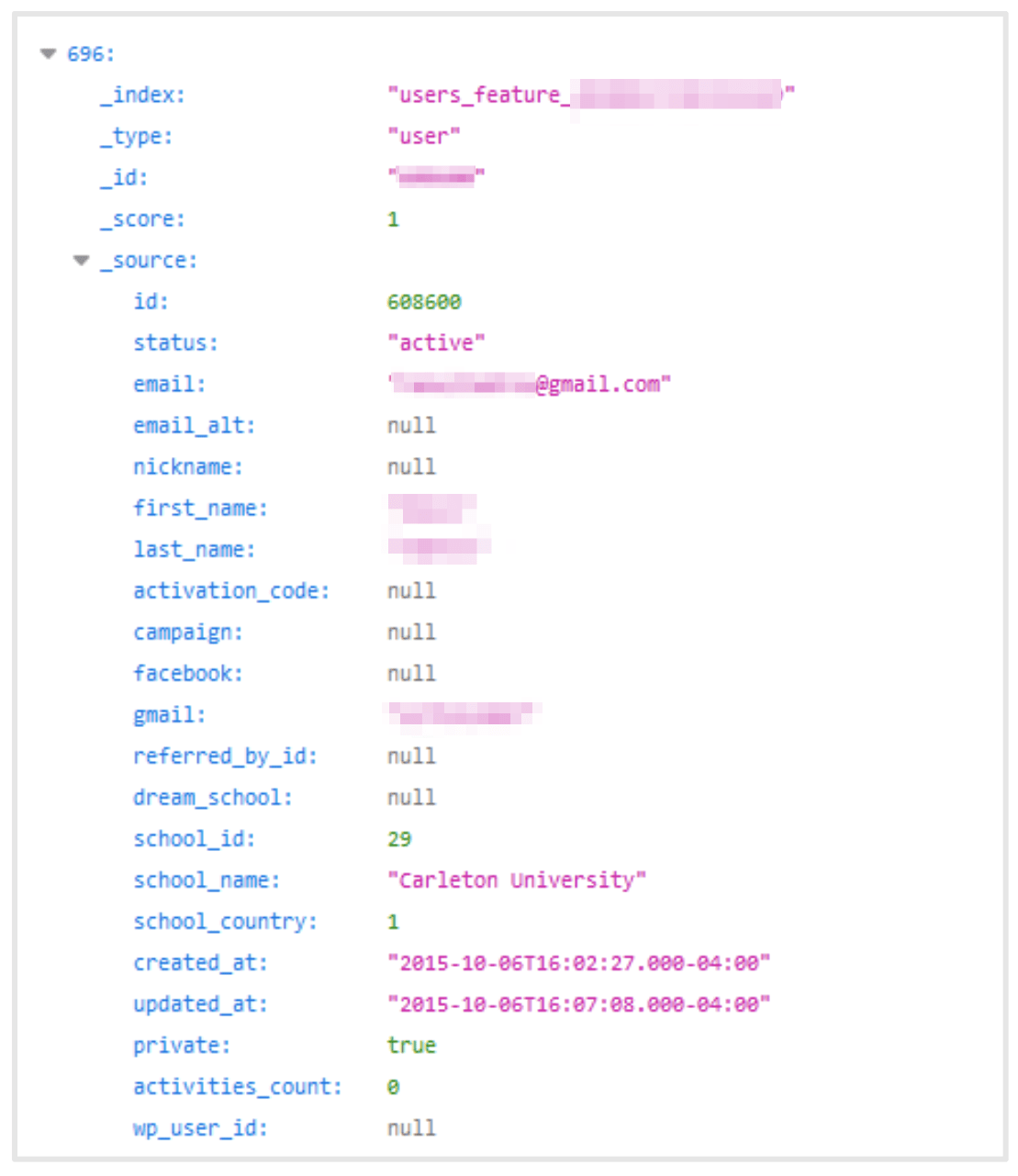
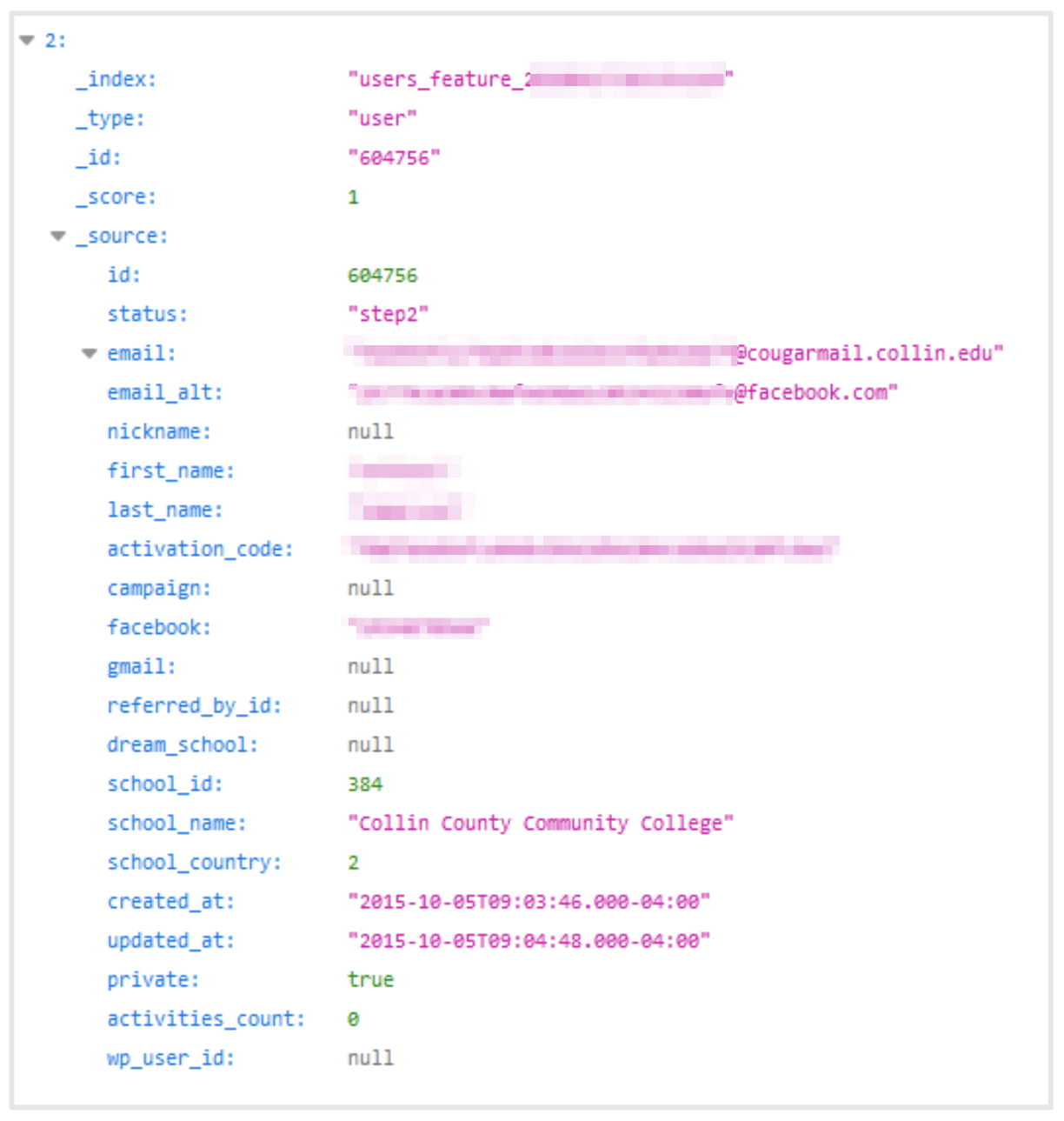
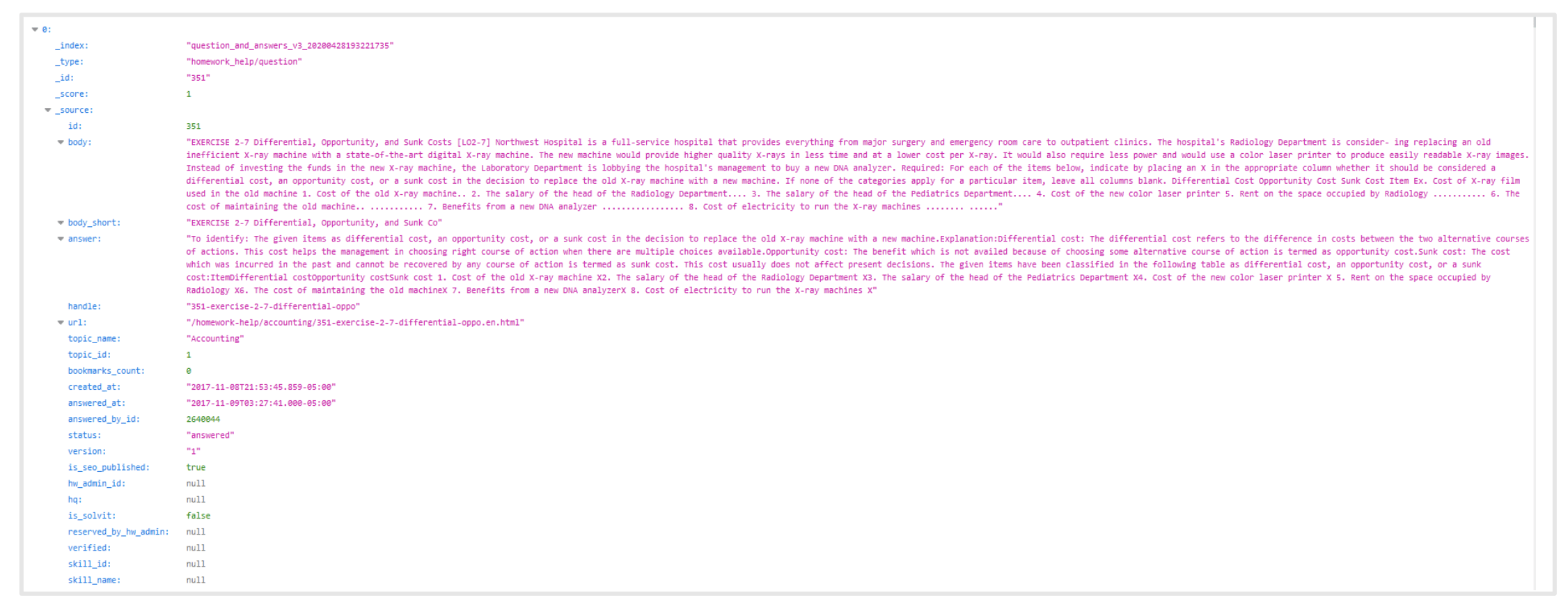
Many records also included additional information on individual students and their courses, including faculty details and access to otherwise protected textbooks and “Question and Answer” exercises.
An example can be seen below:
Data Breach Impact
Had criminal hackers gained access to this database, it would have allowed them to pursue a wide range of illegal activities.
With the PII data stored in these records, they could create effective phishing emails, tricking victims into any of the following actions:
- Providing credit card details
- Providing access credentials for private accounts elsewhere online
- Clicking a link that will embed malicious software on their devices, such as ransomware, malware, and spyware.
As OneClass has a paid subscription plan for premium content and resources, hackers could use this to their advantage when coercing someone into providing any financial information.
Furthermore, OneClass users are very young – including minors – and will generally be unaware of most criminal schemes and frauds online. This makes them particularly vulnerable targets. It’s also likely many of them use their parent’s credit cards to sign up, exposing their whole family to risk.
With so many students relying on remote learning due to Coronavirus, OneClass could be experiencing a surge in new users. Hackers could quickly create fraudulent emails using the pandemic and related uncertainty as a pretext to contact potential victims, posing as OneClass and asking them to divulge sensitive information.
Given the size of OneClass’s user base and the number of people exposed in this leak, hackers would only need to successfully defraud a tiny proportion for a criminal scheme to be financially rewarding.
The impact on their victims could be devastating.
For OneClass
The most immediate impact on OneClass from this breach is the potential loss of users. If people feel the company has endangered them by not protecting their data, they may cancel memberships and leave the platform altogether.
As OneClass depends on partnership with educational institutes and lecturers, they may also experience backlash from both, for the same reasons. If partners were to sever a relationship or restrict interactions with OneClass, the company’s value proposition would drop significantly.
As stated on its website, OneClass user data is subject to the United States’ privacy laws. Furthermore, the company’s servers are located in the US, along with most of its users. As a result, it falls within the jurisdiction of California’s CCPA data privacy law and broader regulations across North America.
The company is thus required to take specific steps in response to this data breach and may face auditing or investigations from regulatory agencies. Such outcomes could take considerable time and even result in fines.
Finally, if OneClass’s competitors had gotten access to this data, it would have allowed them to copy, or improve upon, the business model that has brought OneClass’s success. And now that OneClass failed at keeping its customer data safe, its competitors can also take advantage of the bad publicity the brand is going to receive, and even take over their customers.
All these potential outcomes could have a severe impact on OneClass’s revenue, reputation, and ability to sustain the business through significant uncertainty.
Advice from the Experts
OneClass could have easily avoided this leak if it had taken some basic security measures to protect the database. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online database from hackers.
For OneClass Users
If you’re a customer of OneClass and are concerned about how this breach might impact you, contact the company directly to determine what steps it’s taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users, and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered the breach in OneClass’s database as part of a huge web mapping project. Our researchers use port scanning to examine particular IP blocks and test different systems for weaknesses or vulnerabilities. They examine each weakness for any data being leaked.
Our team was able to access this database because it was completely unsecured and unencrypted.
OneClass was using an Elasticsearch database hosted on AWS, which is ordinarily not designed for URL use. However, we were able to access it via browser and manipulate the URL search criteria into exposing schemata from a single index at any time.
Whenever we find a data breach, we use expert techniques to verify the database owner, usually a commercial company.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to OneClass, not only to let them know about the vulnerability but also to suggest ways they can make their system secure.
These ethics also mean we carry a responsibility to the public. OneClass users must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
Introducing The Leak Box
To ensure our mission has the most significant impact possible, we’ve also built The Leak Box.
Hosted on the dark web, the Leak Box allows ethical hackers to anonymously report any data breach they find online. We then verify and report any submission deemed a legitimate threat to the public’s safety.
We never sell, store, or expose any information we encounter during our security research. This includes any information reported to us via The Leak Box.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data leaks in recent years.
This has included an enormous data leak from a European e-learning platform in almost every country on the planet. We also revealed that a popular digital wallet app had exposed millions of Americans to fraud. You may also want to read our VPN Leak Report and Data Privacy Stats.